- 01 Mar, 2022
- Topic of the Month

1. Introduction
“Hardware is easy to protect: lock it in a room, chain it to a desk, or buy a spare. Information poses more of a problem. It can exist in more than one place, be transported halfway across the planet in seconds, and be stolen without your knowledge.” - Bruce Schneier
We live in a data-rich world. From resource-hungry applications to mission-critical data, terabytes and even petabytes of data are generated and stored by organisations every day. But this data is only valuable (and not a burden) when it can provide deeper business insights for more informed decision-making that helps meet current and future growth goals. Hence, business data ought to be protected from unexpected loss as it literally bolsters and establishes an organisation’s progression and survival.
And yet our hunger for data is constantly growing, and we need more and more mass storage, as we already store all our personal information on our digital devices. Even ordinary people almost smile when they hear a megabyte because the gigabyte has become the unit of measure today, and the terabyte era is in the corner.

Photo by Tookapic from Pixabay
Companies tend to work with a more significant amount of data than an average person. Much of a company’s data is the personal data of their customers or related data that companies need to pay close attention to and exercise great care about.
In the age of digital data, one of the most important tasks for companies is to guarantee the security of the data they store. Data loss is inevitable if appropriate measures are not taken to protect information and data.
Information is more accessible today than ever before. Taking advantage of the possibilities provided by the Internet, we can download large amounts of data to our computer, and security is becoming increasingly important when working with a computer.
Users also spend much more time and energy acquiring information than creating the conditions for safe use. Building adequate data protection and security requires a significant amount of time, competence and money, and many may not pay enough attention to it.
However, in addition to being easy to use, easy to navigate, and searchable, many people do not think that their data could disappear from one moment to the next if the storage on the machine fails.
This article looks for the answer to what data is worth backing up, how often and where to save it, and how to plan or automate your backups. Backups should not be confused with storage: a backup is more than that. The purpose of the backup is that if the original data is damaged or deleted for any reason, you can restore it using the backup.
2. What is a backup?
“There are only two different types of companies in the world: those that have been breached and know it and those that have been breached and don’t know it.” - Ted Schlein
One of the most significant opportunities and, at the same time, challenges of the information society is to manage, protect and store the incomprehensible amount of information that surrounds us today. Today, almost every company accumulates an opaque amount of data that needs to be stored in a safe and usable place.

Photo by Guvo59 on Pixabay
Companies should also pay close attention to GDPR when handling their clients’ data. Besides, they also need to plan and perform backups of their data. We periodically make a copy of our data, which is stored separately from the original: this copy is called a backup.
The most obvious solution to protect electronic information from destruction is duplicating it. It should be copied regularly and stored in a secure location other than the original in information systems and storage media (external hard disk, DVD, etc.). The presence of copies also protects against system and media failure, accidental deletion or modification, and intentional damage.
Our data is likely to change constantly, so we need to back them up regularly. After all, if the goal is to restore lost or damaged data using the backup, we can always restore only the most recently saved backup to the original location that has been modified in the meantime.
As horrible as it may sound, our data that has been modified since the last backup will be lost even if we have a backup (to put it more optimistically, we may say that only the data modified since the last backup will be lost).
How quickly the data can be recovered depends on the technical solutions used for copying and the procedures used to recover the data. The frequency of backups determines how much data can, in principle, be lost between two backups.
Data is the most valuable resource for many organisations, and data backup is the safeguard every company needs to protect against intellectual property loss and lost revenue.
3. Why should I back up?
“My message to companies that think they haven’t been attacked is: ‘You’re not looking hard enough.” - James Snook
Regular backups are as essential as password protection for our data security. Not only is it an effective solution in the event of unexpected system failures, but it is also essential in the fight against cybercriminals.
Backup protects your data from several risks, including cyberattacks, hardware failures, data corruption, natural disasters or even human error. No matter what you protect against using backup, the proper data backup method allows you to go back to the last known good time before the problem occurred.
The value of a file can be anything from entirely insignificant to invaluable, depending on how essential and indispensable or irreplaceable the information it carries.
You need to ensure that your data is protected in accordance with its importance: you need to consider how much damage you may suffer if the file in question is lost, and the investment in protecting it must be weighed accordingly.
Photo by Saydung89 from Pixabay
4. Backup tips to consider
“It is a fairly open secret that almost all systems can be hacked, somehow. It is a less spoken secret that such hacking has actually gone quite mainstream.” - Dan Kaminsky
4.1. The amount of data to be backed up
The size of the data mass you want to secure and the capacity of the external storage device are also important considerations when selecting storage devices. If you want to save a lot of data, choose a CD-ROM, DVD-ROM or external hard disk. CDs and DVDs cannot be overwritten indefinitely. If you want to archive your databases, you also need to think about the lifespan of the storage devices.
4.2. Scalable recovery
Despite exponentially growing backup needs and an increase in the frequency of backups, companies need to ensure that their data is backed up with adequate frequency. They also need to be prepared for the long-term, secure storage and recovery of these copies.
Recovery needs can be very different. These may be just a few emails or data files, but you may need to recover an entire data centre. Recovery after an extortion virus attack requires special care. In this case, a strategy is needed that, while ensuring data consistency, assures that the environment is not re-infected during recovery. It is an essential requirement for systems used for backup to work reliably in a wide variety of situations.
4.3. Easy to use
IT today handles a wide variety of technologies, all of which work differently and require different types of protection. Nevertheless, making backups should not further increase the already significant workload of IT administrators. At the same time, understanding the condition and operation of the backup infrastructure, the continuous monitoring of its capacity, and the backup plan preparation must be integrated into the IT strategy. An easy-to-use backup system should be used to reduce the complexity of IT systems. In addition, you should take advantage of artificial intelligence to optimise or automate your backup.

Photo by Analogicus from Pixabay
4.4. Automation and synchronisation options
Companies are producing more data than ever before. Processes from product development to customer service have been highly accelerated. Downtime or data loss is unacceptable today. Regulations and competition force companies to have strict data protection. Traditional, manual handling of changes is almost impossible on the one hand and indeed leads to security gaps.
Rapid internal changes and growing user expectations can only be addressed in new ways. Privacy-driven data protection can automatically influence change. IT teams need state-of-the-art data protection solutions that enable workflows to perform backup tasks automatically.
4.5. Offline backup at regular intervals
Create an automatic and regularly checked backup which content is not available or modifiable for devices on the same network. File servers, NAS, and other backup storage devices attached as network drives can be viewed and infected in the same way by malicious programs entering the network. In addition to backups, you should restrict the availability of directories on file servers: all employees should only have access to the folder they absolutely need and are entitled to.
In order to prevent harmful environmental effects (fire, water, vapour, magnetic field), theft and damage, it is crucial that the backups are adequately placed and separated in space. In addition to increasing the distance, data availability must also be restricted to protect them physically from unauthorised persons and harmful effects. In addition to using technical and safety devices, restrictions must also be regulated by legal means.

Photo by Towfiqu Barbhuiya on Unsplash
4.6. Vulnerability test
Many fear that they will voluntarily challenge a company’s systems. However, a well-specified, client-regulated, contracted and experienced professional or service provider vulnerability test should come as no surprise. On the contrary, it can point to security vulnerabilities that the client still needs to be improved to ensure that its systems are adequately protected against attacks from the internal network and the Internet.
- Find out where your data is
- Conduct a risk assessment and business impact analysis
- Create a backup plan
- Follow the 3-2-1 backup policy (redundant backups are key)
- Take advantage of automated backup scheduling
- Encrypt your data before/while backing them up
- Follow privacy laws and keep an eye on regulations
- Treat the above as a process and improve it continuously
Although decision-makers understand and want to solve the problems around personal data, data security, and data integrity, the constant, rapid changes in the IT environment make it extremely difficult to solve them successfully.
4.7. Comprehensive protection
Although companies are increasingly using cloud-based solutions, they continue to use a number of locally deployed technologies and run many business-critical applications on them. A comprehensive and heterogeneous strategy should cover what the organisation wants to protect (physically existing, virtual, cloud-stored data) and the form in which this data to be protected (disk, tape, or other data storage) is stored.
4.8. Insights and reusable data
Companies should ensure that copies of the data are available for business and regulatory purposes. A modern backup system’s return on investment (ROI) is not simply due to ensuring data recovery but also other business opportunities to take advantage of data warehousing. In order to use the same data multiple times, the backup system must be able to extract the requested data from the background repositories. It must also allow third-party applications to retrieve and use this data and manage test data securely.
4.9. Safety
Because of the likelihood of their emergence and the impact they cause, ransomware poses a global risk to companies. In addition to encrypting the data used for work, extortion viruses delete background systems and backups, thus erasing the last lines of defence. Companies and organisations can only defend themselves if they make both systems and data part of a cyber defence strategy.

Photo by PublicDomainPictures on Pixabay
Companies operating in regulated industries can only use data-separated copies, unchangeable file systems, and write once read many (WORM) repositories to keep their data intact. IT managers’ responsibility is to develop a practice based on the remote location of data and its disconnection from the live system. Only this can ensure that the malware is not accidentally transferred from the infected file to the recovered copy.
4.10. Cybersecurity processes
The cybersecurity processes need to be regulated and educated within the organisation. Define in the company policy precisely what an employee can do when using the company IT infrastructure (internal network, company notebook, file server, network printer, etc.). The policy should also state that all other activities (i.e. not specified in the policy) are prohibited.
4.11. Confidentiality of the data
When we talk about secure storage, we also need to think about the confidentiality of the data. There is also a solution: the data can be stored encrypted with a unique key on both the machine and the cloud, so if someone accesses the machine or obtains access to the cloud storage, they only get useless data on their own. The data can only be used with a password/key known to the owner.
4.12. Is the backup reliable?
The primary purpose of backing up is data recovery: proper security is only possible if the work environment can be restored from backups in the event of a data loss or system crash. It is also advisable to carry out restorations regularly according to an appropriate strategy. The development of a rescue strategy is not the result of a one-time process but is constantly changing and improving due to the experience gained during recovery.

Photo by Madartzgraphics on Pixabay
5. Causes and consequences of data loss
“If security were all that mattered, computers would never be turned on, let alone hooked into a network with literally millions of potential intruders.” - Dan Farmer
A variety of events can cause data loss, and there is no completely secure system or technology. Although data loss is a real, multi-cause event, few people deal with the secure handling of their data in a planned, systematic way.
What are the possible causes of data loss?
Physical, hardware reasons
- malfunctioning device
- overheating, poor cooling
- dust, dirt
- fracture impact
- steam and water ingress
Software reason
- application crash
- file system corruption
- virus attack
Human factor
- Intentional or incompetent damage
- Failure to observe the required maintenance and safety regulations
- Improper use (accidental deletion)
The best examples of the consequences and causes of data loss are the case studies of data recovery companies.

Photo by Markus Spiske from Pexels
6. Secure storage of data
“You can never protect yourself 100%. What you do is protect yourself as much as possible and mitigate risk to an acceptable degree. You can never remove all risk.” - Kevin Mitnick
6.1. Which is the most secure storage?
It is possible to determine which data repository is more reliable than the other, but it has no particular significance. The flash drive, though reliable, is relatively fragile and easy to lose. The hard disk is an old, mature technology, but errors still occur, and if a slight shock or vibration happens during operation, physical damage to the disk can easily happen.
The SSD drive is modern technology, it has no moving parts in it, so in addition to being much quieter than HDDs, it is also more resistant to vibration.
There are arguments for and against each technology, but the point is not which technology you choose, but how many copies of important data need to be backed up, how many places to store them, and how often back them up.

Broken hard drive by Raimond Spekking
6.2. How should we store our important data?
When it comes to backing up your data, the question naturally arises about how you can securely store your data. Many people think that if there is at least one copy of the data, everything is fine. Almost. Much depends on where the copy is and how recent the backup is. A backup to an external HDD is worth nothing if stored in the same place where the original data: a burglary or a fire can destroy both at the same time. An obvious solution could be a “cloud”. It’s a spatially distributed, multiple redundant, reliable infrastructure-based storage solution that, when used carefully, provides almost 100% security.
It’s just “almost” because you have to think of it as a process: in order to store or backup your data in the cloud, the data must first get to a secure storage location. However, you cannot influence who the cloud provider is, how reliable it is, how often it stores data and protects it from cyberattacks.
You can learn more about cloud technology in a separate article: Cloud security - Is it wishful thinking or reality? There are many different cloud-based technologies and providers that can use other cybersecurity solutions, so it is worth considering this issue properly if you want to find a suitable backup solution.
If you want extra security, you can also back up the data stored in the cloud from time to time, which can be stored in physical storage or at the cloud storage of another service provider.

Photo by Frank R on Unsplash
7. Designing data backup strategies
“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.” - Martina Navratilova
Regular backups result in a large amount of data, so it is a good idea to save only the changes between periodic full backups. Backup software allows this by selecting different types of backups.
7.1. The backup plan
First, make sure you have a data backup plan, as this is the starting point for backup and recovery activities, no matter what industry you work in.
One of the first steps in creating a contingency plan is to conduct a risk assessment and business impact analysis. The risk assessment identifies issues that could adversely affect the organisation’s business. Business impact analysis identifies the potential effects of disruptions in an organisation’s operations. These assessments are crucial to disaster recovery plans, but they can also provide valuable information on what and how to back up.
The backup plan should specify what data should be backed up and the frequency of backups. Some data may not require backup, while critical data may require continuous ongoing data protection.
The backup plan details the organisation’s data backup process: who performs it, what programs are used, where the backups are located, and so on. In addition, the plan includes a process for testing, reviewing, and updating the backup plan.

Photo by Turmfalke on Pixabay
7.2. Backup strategy
Developing the right data backup strategy and a set of rules is a complex task that requires expertise. In the case of larger companies, the appropriate security rules, even broken down by organisational unit, must be developed as a separate task in accordance with the applicable rules based on security policy.
The security rules for the organisation are set out in the IT Security Policy, which requires a careful review of standards, recommendations and the relevant legal background. We can distinguish multi-level security based on the sensitivity of the data processed and the critical nature of the system operation.
Backup software settings can only be set successfully and efficiently based on a carefully planned backup strategy.
7.3. Work environment survey
To develop an effective backup strategy, you need to know your own IT infrastructure. To put it very simply, this means that you need to be aware of the nature of your data, where your data is generated and how it is stored. You can think about automating the backup process as efficiently as possible if you know this. At this point in developing a backup strategy, you need to ask yourselves the following questions as follows:
- What hardware configuration is my data stored on?
- What operating and file system am I using?
- What applications shall I use (how shall I store my data)?
- What data storage devices are used and how (frequency, mobility, environment)?
8. Types of backups
“We should treat personal electronic data with the same care and respect as weapons-grade plutonium – it is dangerous, long-lasting, and once it has leaked, there’s no getting it back.” - Cory Doctorow
Another critical question, the answer to which will also affect the efficiency of your backup system and the cost of the process. Depending on the frequency of use and modification of the data, we determine the schedule of backups.
It is good to perform complete system backups before and after major hardware or software upgrades or reconfiguration. In the case of work data, it is advisable to save them depending on the hours worked and adjusted for major changes. The timing of backups can be automated, with individual applications and backup programs allowing you to set the timing of automatic backups.

Photo by OpenClipart-Vectors on Pixabay
8.1. Full backup
You may choose to back up all your data (full backup), but given that it is usually a substantial amount of data, it can be a time-consuming, demanding, and expensive process.
Also, keep in mind that the time it takes to restore your data can be very long with a full backup, which means a regular business can only be restored after a long time. In our fast-paced world, one of the things every company wants to avoid is downtime or unavailability, which can come at a considerable cost.
Of course, this decision also depends on the industry in which you work, as it is often determined by the nature of the data how vital the data is (you need to be sure that no data loss occurs). This is not even a question, for example, in the banking sector, military, and critical industries, as storing, managing and backing up data is extremely important.
8.2. Incremental backup
An incremental backup is much faster than a full backup: in an incremental backup, the only data that is backed up is the data that has been changed since the last full- or incremental backup.

Incremental vs Differential Backup, & Full – Explained – Youtube
8.3. Differential backup
A differential backup backs up only the files that changed since the last full backup (and not since incremental backups). Suppose you do a full backup on Sundays. On Monday, you back up only the files that changed since Sunday; on Tuesday, you back up only the files that changed since Sunday, and so on until the next full backup (Sunday). Here, you do not use incremental backups. Therefore, incremental backups are sometimes called “differential incremental backups,” while differential backups are sometimes called “cumulative incremental backups.”

Incremental vs Differential Backup, & Full – Explained - Youtube
To understand the difference between full, incremental, and differential backups, what data is required for the backup, how long it takes to restore the data, and how long the three backup procedures take, check out the video above. The sketch below provides a quick overview of the differences as follows:
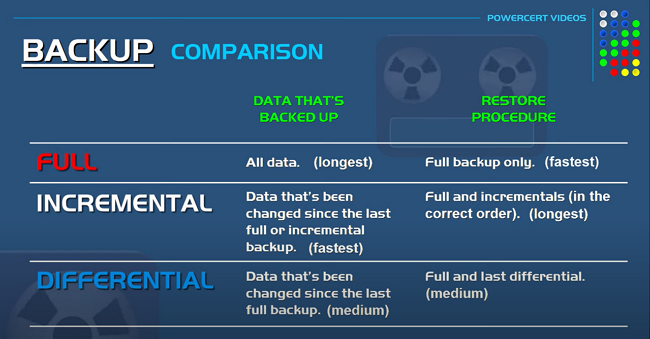
Incremental vs Differential Backup, & Full – Explained - Youtube
Personal data is becoming more and more valuable, and its protection and thus its backup is an increasingly critical issue that companies need to address.
You may use different strategies when backing up data and system files. Ensuring the integrity and usability of the data is a much simpler task than recovering the elements operating the system in the event of an error.
9. The 3-2-1 backup strategy
“The knock-on effect of a data breach can be devastating for a company. When customers start taking their business—and their money—elsewhere, that can be a real body blow.” - – Christopher Graham
Teleworking is particularly risky from a privacy standpoint, as cybersecurity may not be as strong on the home network, and users work on less secure personal devices. Cloud-based backup is becoming more valuable as an external resource in a remote work environment.
The 3-2-1 concept is a golden rule that should be used by companies and individuals alike. In this concept, you should have three instances of data, at least two of which are stored on different media types, and one instance is located in a physically different location, away from the previous two. This strategy is visually well illustrated in the image below:
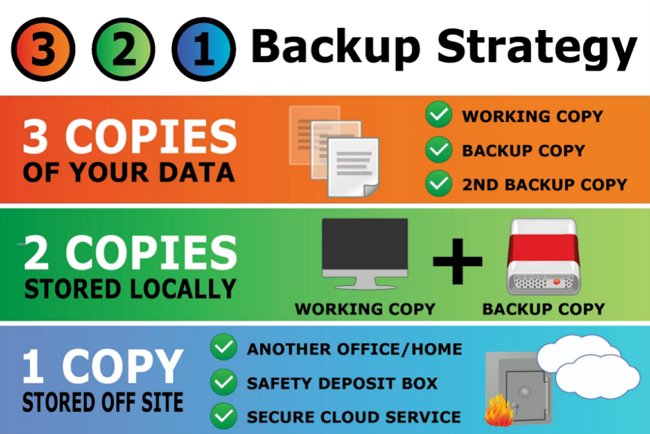
The 3-2-1 backup strategy (drivesaversdatarecovery.com)
10. On-site vs off-site backup
“If you think technology can solve your security problems, then you don’t understand the problems, and you don’t understand the technology.” - Bruce Schneier
10.1. On-site or local backup
An on-site or local backup is a copy of data stored on local storage devices, such as hard disks or magnetic tapes. Off-site backups are stored remotely, usually through cloud-based backups or on tapes that are physically transported to another location.
The most significant advantage of an on-site backup is that it allows faster and easier access to data, making data recovery much easier and faster in the event of a data loss.
Although offsite backup is stored on a physically different location and thus provides much greater security for data recovery in the event of a fire, for example, retrieving data from the cloud or an external location can be much more time-consuming.
This brief video by TechTarget illustrates and compares the advantages of on-site and off-site backups.
TechTarget: On-Site vs off-site data backup
10.2. Off-site or cloud-based backups
“The cloud is an idea linked to the concept of distributed computing – a system whereby the hardware, software, and processes making up an IT system may be situated at different locations across the globe, so long as they remain in contact with each other via some sort of communications network.” – IT Chronicles.
Thus, in the context of cloud-based backups, the element of the 3-2-1 strategy is realised that you need to store your data in a different location in space (and not locally on the company’s servers, local drives, etc.).
Because the data is not stored locally but must be transported to a different location for backup, it is necessary to check the security of the data during transmission and storage.
In the cloud, not only giants or medium-sized enterprises but also individuals can upload their data and files. One way or another, you can usually store large amounts of data in the cloud during storage, and it can take a long time to back up your data.
Care must be taken to ensure that the data can be restored as soon as possible, so make sure you have enough bitrate to download the data within a reasonable time. To keep this time short, make sure you choose a good backup strategy that includes local data storage and storing data in the cloud in the event of a disaster, such as a fire.
Data loss can seriously impact your ability to continue business services. Storing local data in the cloud is also a safety measure since having your data at multiple secure off-site locations via the cloud makes catastrophic data loss less likely.
We may conclude that having on-site and off-site backup is critical for secure data backup and disaster recovery. For more information about the cloud, consider reading the following article Cloud security: Is it wishful thinking or reality?
11. Figures and statistics
“Being too busy to worry about backup is like being too busy driving a car to put on the seatbelt.” - T. E. Ronneberg
There is a wealth of data and statistics on the Internet about how frequent data leakage and data loss is, how much financial damage it causes, and how often companies and individuals back up.
We cite three sources in this chapter. BackBlaze is a company that provides robust, scalable, low-cost cloud-based backup and storage services. We first cite a few data from the BackBlaze survey and then give some pertinent data from the Ponemon and IBM Cost of a Data Breach Report 2021. The latter report analyses the financial costs of data leakage
Finally, we selected data from Cybersecurity Ventures on the frequency of cyberattacks.
11.1. Backblaze figures
Backblaze conducted a survey between 2008 and 2021 on how often people back up their data. Depending on the point of view, the data can be very worrying, shocking, or even reassuring. If we look at how many (20%) still never back up their computers, the data is shocking, but when we look at the numbers as a function of time, we see a positive trend: in 2008, 35% of those surveyed (!) never performed a backup.
The number of backups performed daily, weekly or monthly basis shows an increasing trend in the long run, albeit at a very low rate between 2008 and 2021.
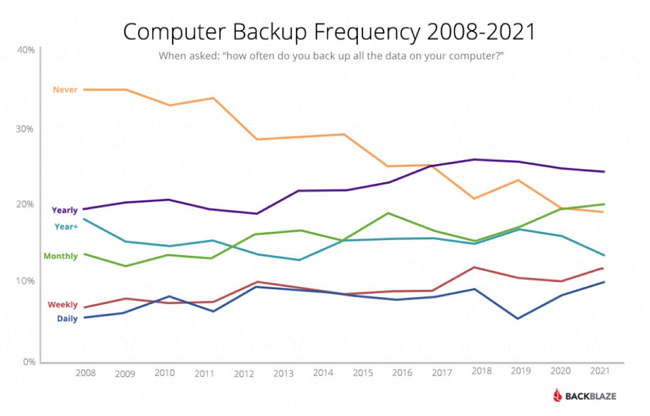
Backup frequency (2008-21) survey by BackBlaze
The pie chart shows the trend itself and a more accurate picture by displaying the percentage of data, which indicates that the shift is broadly positive. More and more people are recognising the need for backups, and we are seeing more and more people performing backups. However, if we look at things in absolute terms, there is still room for improvement: many people do not back up often enough (not to mention those (20%) who never do).
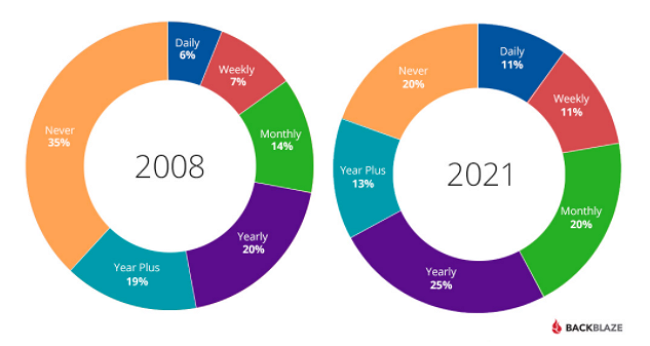
Backup frequency (2008-21) survey by BackBlaze
After the data above, take a closer look at the data for the 20% who never make a backup. Given that the best way to protect against malware and ransomware is to make up-to-date backups, the data of these people are fully exposed to cyberattacks.
If we only talk about ransomware, we can still say that the situation is dramatic, as such attacks occur in general every 11 seconds (and their frequency is constantly growing).
‘Ransomware is expected to attack a business every 11 seconds by the end of 2021.’ – Steve Morgan, Editor-in-Chief, Cybercrime Magazine
And the trends are not only worrying but rather shocking. As per the European Union Agency for Cyber Security (ENISA), the number of extortion virus attacks increased by 150% between April 2020 and July 2021. Basically, people who never back up risk losing all their data irrevocably. In terms of the severity and frequency of cyberattacks, not backing up is irresponsible since it is only a matter of time before these computers become infected and their data becomes corrupted or encrypted. Based on a survey by BackBlaze, among those people who own their computers
- 62% have lost data at some point
- 76% have deleted something by accident
- 51% have had an internal or external hard drive crash
- 52% have lost access to their data
- and 61% had a security incident.
11.2. Cost of a Data Breach Report 2021
- Every 39 seconds there is a cyber attack
- Most companies take nearly 6 months to detect a data breach
- 95% of cybersecurity breaches are due to human error
- 4 million files are stolen every day – that is 44 every single second
- Only 57 percent of businesses are successful in recovering their data using a backup
- Ransomware cost the world $20 billion in 2021
- The cost of ransomware is expected to rise to $265 billion by 2031
- Recovering from a ransomware attack cost businesses $1.85 million on average in 2021
- 43% of cyber attacks target small business
- More than 77% of organizations do not have a Cyber Security Incident Response plan
The Cost of a Data Breach Report 2021 was created by the Ponemon Institute and IBM. As per the Report, the average total cost of data leakage increased from $ 3.86 million to $ 4.24 million in 2021. What is more, 2021 had the highest average cost in the last 17 years.
The findings of the report also showed that the overall increase in the average total cost was due to slower response times because of teleworking. For companies where more than 50% of the employees worked remotely, it took nearly 316 days to find and prevent the infringement, compared to the usual 287-day average.
The report also indicated that time has significant importance in the extent of the material damage to a data breach: businesses can save up to 30% if they can restrain a data breach within 200 days.
The Report also revealed that the total average cost of a ransomware attack was $ 4.62 million (more expensive than the average cost of a data leak, which was $ 4.24 million).
The Data Breach report also states that the most common cause of data leaks was the theft of user credentials. These are responsible for 20% of the violations, causing an average of $ 4.37 million in damage.

Photo by RostyslavOleksin on VistaCreate
11.3. Cybersecurity Ventures
And the process is far from over; moreover, according to Cybersecurity Ventures, the cost of ransomware is expected to reach $ 265 billion by 2031.
Not only is the number of users and devices in use exploding (more and more people are using computers, laptops, smartphones or some IoT devices), and so are the number of malicious players. But attacks are becoming more frequent, systematic, and sophisticated and causing more and more damage.
Cybersecurity Ventures predicts that the frequency of these attacks will increase in the future: there will be a new attack every 2 seconds, and hackers will refine their activities further.
And according to many indicators, companies and individuals are often very unprepared or careless. 95% of all data leaks are due to human failure, and a cyberattack occurs every 39 seconds, with 75% of attacks starting with a malicious email.
On average, only 5% of corporate folders are adequately protected, and 21% of files are not protected at all. It is no surprise that about 4 million files are stolen every day (44 files per second).
After the above terrifying data, it is evident that backing up is crucial because if - for any reason - we are unable to protect our files adequately and they become infected or unusable, we can continue working by using our previously backed up files.
12. How the pandemic changed our backup habits
“You may think that Ransomware attack decrypts the encrypted data after Ransom payment. Don’t forget the fact that 97% of the attack victims haven’t recovered, even after a ransom.” - Arulselvar Thomas
The epidemic had a significant impact on backup activities. The explosive spread of telework has put people and companies alike in a whole new situation. The privacy adequacy of the backups and the protection of countless new remote endpoints from one moment to the next have been a particular burden, especially for companies. However, the pandemic has also made individuals more vulnerable to cyberattacks.
Businesses had to invest in laptops, tablets, smartphones, or even printers for remote employees. They also had to redesign networks and applications to allow large-scale remote access.
With the rise of cloud-based work, the ability to protect cloud-based data has increased, and the new situation has highlighted the importance of cloud-to-cloud backup, too. Meanwhile, the move to telecommuting has forced organisations to rethink and redesign their data protection and backup strategies.
Today, teleworking has become almost a good practice, and many companies and individuals have settled into it. Some jobs appear to remain in this mode even after the pandemic subsides.

Photo by Edward Jenner from Pexels
12.1. Local backups first
During the first couple of weeks of the pandemic, employees were asked to backup data locally to removable media. Workers started working from home, and the safety of these endpoints was often highly questionable. In addition, companies, where home workers have been using VPN since the first moment of a pandemic, had to cope with growing demands for VPN access and often even with limited bandwidth, as local area networks were not designed for this.
Backing up data to local removable media raises cybersecurity issues and questions about the licensing of the backup software you use (if any). And once employees could switch to a secure, remote backup system, they had to securely erase local backups to prevent a backup solution from becoming a data compliance problem.
12.2. Backing up to the cloud – and cloud-to-cloud backup
Backing up user data to the cloud seemed to be an excellent alternative to address the issues mentioned above (limitations of enterprise VPNs and privacy concerns for remote backups of remote workers). It is easier and more reliable for users to back up their devices directly to the cloud. It should be great ease for the company to comply more seamlessly with privacy standards. In addition, cloud-to-cloud backups are becoming more common. The pandemic has moved more and more applications from the data centre to the cloud, and ensuring full data backup has become vital.
12.3. Centralised backup management
The epidemic and the associated challenges have increased the workload of IT teams. As a result, they sought centralised tools to protect data regardless of location. The solution was to back up user data directly to the public cloud.
12.4. Protecting SaaS applications
Software as a Service (SaaS) has been one of the technologies that helped organisations adapt to pandemic working. Because of this, backups for SaaS applications have become more critical than ever.
12.5. Ransomware
The increase in the number and intensity of extortion virus attacks has been another unfortunate side effect of the pandemic that influenced corporate backup strategies. Many ransomware attacks have been Covid-related phishing campaigns and attacks against the pharmaceutical and healthcare sectors.
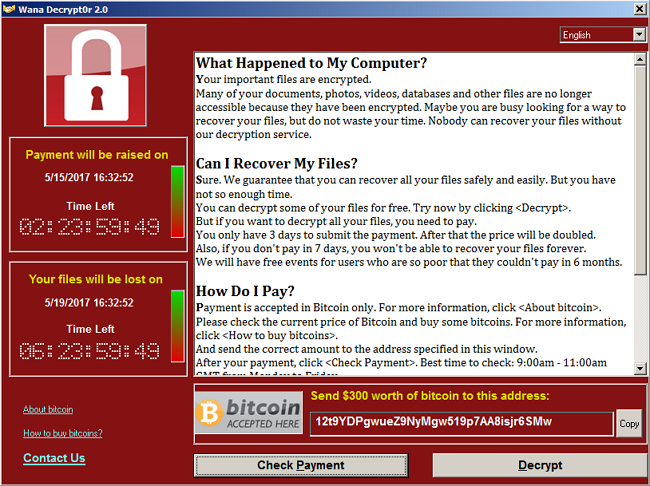
Wana Decrypt0r 2.0 warning window (MySpyBot)
Cyberattacks pose a constant threat to organisations, and ransomware has become the number one security risk to businesses and users. Not only are ransomware attacks more severe, more targeted, and more harmful, but their frequency is increasing dramatically and steadily. Therefore, the annual cost of extortion viruses to organisations worldwide is rising sharply.
Indeed, you cannot turn a blind eye to ransomware attacks: the only defence against them is creating backups.
13. World Backup Day
“Companies spend millions of dollars on firewalls, encryption and secure access devices, and it’s money wasted; none of these measures address the weakest link in the security chain.” - Kevin Mitnick
13.1. History of World Backup Day
World Backup Day is celebrated on the 31st of March each year. Initially, it was World Backup Month and started by a hard drive company called Maxtor (later acquired by Seagate Technology). This day is an excellent opportunity to keep track of your backups.
13.2. Why is it important to celebrate World Backup Day?
We have to admit that many of us are postponing creating backups because we think we are going to do the backup the next day: “we don’t have time to deal with that right now”. As per the research done by Backblaze, about 20% of people have never taken any backup for their important files.
However, we are all aware that if there is no backup and data loss occurs, we cannot restore our lost files. We can say goodbye to our precious family photos or any unique event or memory, such as our graduation video or the first photo of our child.
13.3. How to observe it?
The best way to celebrate World Backup Day is to take the time to back up your data. How and what storage space to back up is secondary. Make sure you take a backup from your smartphone, tablets, laptops, and other electronic devices on this glorious day. It is time (if you have not done it already) to use quality cloud storage services and make backups to prevent data loss due to crashes.

World Backup Day by Christine Berry (ChiCorporation)
14. How can SECURITYMADEIN.LU help?
“If you think you know-it-all about cybersecurity, this discipline was probably ill-explained to you.” - Stephane Nappo
14.1. SECURITYMADEIN.LU
SECURITYMADEIN.LU is the cybersecurity agency for the Luxembourg economy and municipalities. It provides extensive cybersecurity expertise and solutions to SMEs and companies of all sizes and municipalities through its three departments: CIRCL, CASES and C3, in close collaboration with the CYBERSECURITY Luxembourg ecosystem’s players.
14.2. CASES
CASES (Cyberworld Awareness and Security Enhancement Services) is part of SECURITYMADEIN.LU. It has multiple services available for the public to raise awareness concerning cybersecurity. Below, you can read some advice from CASES for small businesses to store and back up their data securely.
Start-up and small business owners need to focus on the problems associated with every process in their business and so dealing with cybersecurity and backup-related issues are just one of those problems they need to face. However, they need to be aware that data loss can occur in several ways. To avoid possible data loss, take the following steps:
1. The first and most crucial step is to know where your data is: where you store them, what types of data, and how you store them?
2. If you already know where you store your data (on which servers, drives, etc.), you can start thinking about the types of failures, problems, threats that can lead to a data loss. Make a list of the most common problems you may encounter and start describing areas where you think you may be in danger.
3. Do you use a cloud storage provider to store your data? If so, what types of files get backed up there and how often? How does the provider handle their hardware failures? What is the availability time, and what is included in the SLA (service level agreement)?
4. Be aware of software-based bugs or attacks. What would happen if a virus accidentally entered your network? Keep in mind that some malicious programs are designed to steal your data, while others, called ransomware, simply deny access to your data until you pay the ransom (without a guarantee of data recovery). An antivirus solution is a good start, but these programs cannot recover your data if it is damaged or closed.
5. After analysing the risk of software attacks, assess the risks associated with your hardware: what would happen if your company’s hardware or devices were stolen?
6. After gathering the risks to your business data, you need to examine which data is critical to your day-to-day operations and which is not. This categorisation needs to be done because it usually generates so much data, especially for companies, that saves much space and requires a lot of storage space, which can cost a lot. By taking the time to identify and locate the different types of data you have, you can make better decisions about which data should be protected and which data would be irrelevant if lost.
7. Now that you have catalogued your risks and prioritised your data, the final step is to decide how best to protect it.
A solution can be cloud-based storage, which ensures that your data is stored separately from your site and can be accessed at any time by any means. It is always worth carefully examining your cloud service contract. There may be limits and conditions on recovering data in the event of a failure.
More and more applications are cloud-based, which means that your data is no longer stored on your devices or internal network. This is not to say that they are not secure, but you should be careful when choosing your service provider and packages.
You need to know how the owner of the service provider stores and protects your data. Your service provider should give you the option to back up your data or even retrieve your data in a format that you can easily use in the event of a service outage. Ideally, you should be able to check that backups are available and, if necessary, reliable.
In addition to the above, we recommend storing at least one copy of your critical data in a location other than your physical office.
Instead of relying entirely on a cloud provider for your data, create and implement your security plan alongside the cloud provider, follow a 3-2-1 backup strategy, and run automatic backups at regular intervals.
CASES provides additional valuable tips on backup in the video below:
CASES – Data backup (YouTube)
14.3. CIRCL
The Computer Incident Response Center Luxembourg (CIRCL) is also part of SECURITYMADEIN.LU, with the initiative to gather, review, report and respond to computer security threats and incidents. CIRCL is the CERT for Luxembourg’s private sector, communes, and non-governmental entities.
You can report security incidents to CIRCL: they are like firefighters who take action when an incident has already occurred. They investigate, identify the incident, analyse the malware, and do reverse engineering – among other things.
During the 41st edition of the monthly Cybersecurity Breakfast organised by SECURITYMADEIN.LU, Security Researcher at CIRCL, Alexandre Dulaunoy, talked about the more common ‘Data Breaches: The dirty business behind the scenes. When your leak becomes the product.’
Cybersecurity Breakfast #41 - Data Breach: The Good, the Bad and the Ugly
15. Conclusions
“Security in IT is like locking your house or car – it doesn’t stop the bad guys, but if it’s good enough, they may move on to an easier target.” - Paul Herbka
Prevention remains the most effective solution for protection. You need to follow a couple of simple steps to avoid infecting or corrupting your data: keep the software up to date, use a reliable antivirus, be careful when clicking on attachments or visiting unknown websites.
In addition to the protection options and steps mentioned above, backing up is an infinitely simple yet often missed protection solution. Companies have the professional background and workforce to develop appropriate backup procedures. This may be missing for small businesses or individuals, but backing up is usually very simple.
We cannot stress enough that a system is as strong as its weakest link, which is true here, too, as these simple steps must be taken together, not neglecting or omitting any of them to protect your systems from attackers.
The value of a piece of data is revealed when it no longer exists or cannot be restored. The situation is similar to how many people relate to their health: most take it for granted until their health is shaken.
For companies, personal and confidential information loss has severe legal and financial consequences. For individuals, data loss means the loss of personal information, which is a significant problem, especially if files containing our personal memories (marriage, memorable vacation, family videos, childbirth, etc.) are lost.
Back up your digital life, stay vigilant and prepare for the worst: this is the only way you can protect your digital footprint and save your files for the future.


