- 01 Jan, 2022
- Topic of the Month

1. Introduction
“Privacy is not an option, and it shouldn’t be the price we accept for just getting on the Internet.”
- Gary Kovacs
In our Internet era, we are constantly giving and receiving information, leaving traces of ourselves on the World Wide Web. Also, cameras lurk on all means of public transport or in the streets, not to mention the gates or other data collection equipment at airports and public institutions. But you do not even have to leave your home today for others to observe and collect data about you.
An average citizen in the information society is becoming “virtualised” and communicates with more and more people and organisations with complete impersonality. However, the opposite is also true: for companies, organisations and decision-making authorities, an average person appears only as data or a set of data.

Image resource: VistaCreate by Vadim Vasenin
Many online services require users to provide certain personal information in order to use their service. Many users are willing to give out their personal information without thinking about who, where, how, for how long will they store that piece of information, or will they sell it to another service provider? Before providing personal information, users should think about what can be done with it and assess whether they are still willing to pass on that information.
Because of unstoppable virtualisation, individuals need to control the data that flows from them to the outside world. In addition to the appreciation of the role of the individual in the digital world, the need to protect their privacy also requires increased attention and legal protection.
The GDPR pursues a dual, seemingly contradictory goal: the free movement of personal data within the European Union and the protection of privacy and personal data.
Like cybersecurity itself, data security and protection are multi-actor issues. Everyone involved has a responsibility: users need to consider how much they are sacrificing and sharing from their private sector, while those who process their data need to know what legislation they need to comply with.
2. Data privacy
“Privacy is one of the biggest problems in this new electronic age.”
- Andy Grove
Privacy is the state or condition of being free from being observed or disturbed by other people. In general, it is the right to be left alone from intrusion and interference.
In the case of data privacy (also called ‘information privacy’), this means that our data may not be accessed or modified by others unless we have given our prior consent or explicitly requested it. That is, information privacy is the right to control how your personal information is collected and used.
Data privacy also refers to the proper handling, processing, storage and use of personal data. Data privacy is about the rights of individuals concerning their personal data.

Image resource: VistaCreate by Andrew Lozovyi
Data privacy also focuses on how data is collected, stored, processed, and shared with third parties and compliance with applicable data protection laws. However, data privacy is not just about the proper handling of data but also about the public expectation of privacy. The focus of data privacy is always on the rights of individuals.
2.1. Elements of data privacy
Data privacy includes 3 elements:
- Right of individuals to be left alone and to have control over their personal data
- Procedures for the proper handling, processing, collection and sharing of personal data
- Compliance with data protection laws
Data protection laws worldwide aim to give individuals back control over their data, empowering them to know how, who, and why their data is used and regulate how their personal data is processed and used.
3. Data security
“Increasing cyber-physical system complexity brings security challenges as well as privacy challenges.”
- Dan Lipinski
Data security is a system of technical and organisational solutions to prevent the unauthorised acquisition, modification and destruction of data.

Photo by FLY:D on Unsplash
Data security includes a set of standards and measures that an organisation takes to prevent unauthorised access to digital data by third parties or the intentional or unintentional alteration, deletion or disclosure of data. It focuses on protecting your data from malicious attacks and preventing the use of stolen data (data leaks or cyberattacks).
Data Security practices and processes may include:
- activity monitoring
- encryption
- breach response
- network security
- access control
- multi-factor authentication
At the heart of data security is the protection of personal data against unauthorised access or malicious attacks by third parties and the exploitation of data. It is designed to ensure the protection of personal data using a variety of methods and techniques to protect your data privacy. Data security ensures the integrity of the data, so the data remains accurate and available to authorised parties.
4. Data protection
“If you care about privacy online, you need to actively protect it.”
- Roger Dingledine
Data protection means the protection of the person, in other words: the protection of the data subject, not the protection of the data itself.
Due to the development, expansion and constant change of the Internet (e.g. the spread of cloud-based technology, IoT, etc.), the requirements that increase data protection for the benefit of the data subject are becoming more and more critical.

Image resource: VistaCreate by Andrew Lozovyi
Data protection is the restriction of the collection, processing, and use of company data and the set of data management tools and methods that ensure the protection of the persons concerned.
It is essential to protect non-public information stored on the company’s network from unauthorised access and to make the data available to those authorised within the network at all times.
Data protection protects information within the company, protecting the entire network. Data protection professionals avoid damage to computers and networks and eliminate and prevent human error and intentional damage. Data security is within data protection, as data security is also about protecting information. However, here, professionals are specifically protecting the documents within the network so that they cannot be accessed, modified or read by unauthorised people.
The right to self-determination of information is the right of the individuals to decide whether to disclose information about them, while the right to data protection imposes restrictions primarily on the data controller concerning the processing of data
Legal regulation of data protection became indispensable when, thanks to the Internet, remote networks were interconnected and thus made it easier for different data to be associated with each other (comparison, analysis, etc.). It has become much easier to access various personal data and business secrets, so it has become inevitable to regulate who, what data, and how you can handle and use it within a legal framework.
Types of data
· Personal data: All information used to identify or contact any natural person. The data is considered personal as long as the personality of the individual can be deduced from it. The person can be identified by name, address, personal ID, etc.
· Special data: Legal protection is based on the fact that the data most in need of protection in data privacy and unauthorised access can cause the most significant harm to the individual. Such special data may include personal data relating to racial origin, national and ethnic origin, political affiliation, religious or other beliefs, state of health, sex life and criminal history.
· Data of public interest: data in the management of a body or person performing a state or local government task and other public tasks specified by law, which do not fall under the concept of personal data.

Photo by Mika Baumeister on Unsplash
Data security is the science of providing technical and organisational solutions to prevent the unauthorised acquisition, modification, and destruction of data. Data security is a smaller corner of data protection. Data protection protects information globally from unauthorised access, while data security protects it more narrowly.
5. Data protection vs data privacy
“With the evolution of information technology, there have emerged new questions, for example, of data and privacy.”
- Ram Nath Kovind
Data privacy and data protection are very closely related, so much so that people often think of them as synonyms. But it is essential to understand the difference between data privacy and data protection to know our responsibilities and rights as users (data subjects) and the role and responsibilities of service providers.
Data privacy concerns arise at any time when personally identifiable information is collected, stored or used. In contrast, data protection concerns arise when there is a possibility of data leakage: the provider cannot guarantee the protection of our data from unauthorised access.
Data protection answers the question of what those who have lawfully collected your data can do with it and what control they have over the retention and use of the data. Data privacy focuses on how to collect, process, share, archive, and delete data in accordance with the law. On the other hand, data protection ensures that your data is safeguarded from unlawful access by unauthorised parties.
That is, data protection is about securing data against unauthorised access. On the other hand, data privacy is about authorised access: who has it and who defines it. Data privacy is a legal issue, while data protection is essentially a technical one. We cannot ensure data privacy unless personal data is protected by technology.
If someone can steal your personal information, your privacy is not guaranteed anymore, putting you at risk of identity theft or other security breaches. But technology alone cannot ensure privacy protection. Privacy protection protocols remain vulnerable to authorised individuals who might access the data. However, the biggest challenge for these authorised individuals is the extra responsibility over data protection laws, not the technology itself. In short, there is no technological guarantee that could replace the central role of trust in ensuring data protection.
The only protection that personal data can rely on during transmission is encryption, so an unauthorised third party can see the data but not read or collect it. For further reading on this topic, please read the article Encryption: the unnoticed law enforcement force in cyberspace.
The fundamental distinction between data privacy and data protection depends on whom we want to share information with rather than how we want to protect the shared data from everyone else.
One is about regulation; the other is a technical issue
Data protection focuses on protecting devices from unauthorised use, while data privacy determines who is authorised to access data. It comes from the above that while data protection is mainly a technical task (so we can protect our devices), data privacy is more of a legal issue (we can legally regulate who can access the data).
User controls privacy; companies control protection
The responsibility for setting privacy settings rests primarily with users: they are the ones who control what they share and with whom. It is another issue that many users do not pay much attention to this; they just want to use that particular app and not fiddle with privacy settings that are often hidden. However, data protection is the responsibility of service providers: companies must ensure that the level of data protection set by users is met and their data on the network is protected.
Different approaches, different experts
Data protection focuses on protecting organisations’ assets and is mostly about keeping threats away. Data protection is provided mainly by IT staff with a technical background. On the other hand, data privacy is about what happens to people’s data. It handles and manages data within the organisation, so data protection teams usually consist of experts with legal and policy-making backgrounds.
Privacy first, protection second
Users should first declare what data they want to share and with whom. Then data protection can take into effect to protect the shared data according to the user’s conditions and requirements. The first step in avoiding risk is to question whether it is necessary to provide user data at all. It is then only possible to develop the procedures and technical solutions to ensure the protection of the shared data.
Protection from sales or hacks
User-controlled data privacy is about not selling or sharing your data. In contrast, data protection from a service provider is focused on preventing this information from falling into the hands of unauthorised people (such as hackers).

Photo by Josh Shaw on Unsplash
Privacy without security is worth nothing
Without security, data privacy is worth nothing: no matter how we determine what data we want to share and with whom if our data is insecure. There is no guarantee that our data will not be accessible for other people we initially did not intend to share.
We need them both
One does not provide the other, and we need them both to work together as a proper control mechanism. But do not forget that technology alone cannot ensure personal data privacy.
Humans make technology, and the way we use a specific technology depends on our decisions. Rules and regulations help us in decision-making because if we know ‘the rules of the game’ and are aware of the consequences of our decisions, we may make better decisions.
Although data security can exist without data privacy, such data collection would not take place on a valid legal basis, i.e. it would be unlawful.
6. Why is data privacy important?
“Anyone who steps back for a minute and observes our modern digital world might conclude that we have destroyed our privacy in exchange for convenience and false security.”
- John Twelve Hawks
Individuals expect organisations to learn how to process personal data while protecting individuals’ data privacy preferences. From a business perspective, protecting personal information and emphasising data privacy can positively affect your organisation. Those positive effects can be as follows:
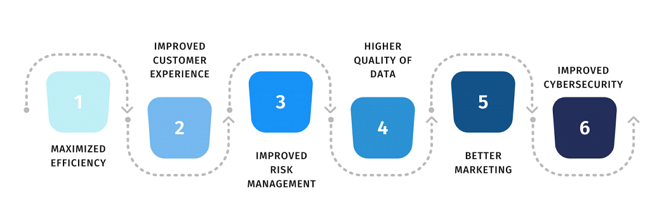
Source: DataPrivacyManager
In our current data-driven world, the true corporate value often lies in companies’ data about their customers. Today, data is an asset worth protecting and preserving. However, companies are constantly forgetting that the data they collect and manage about their customers is not their own; they only ‘rented’ data from their customers.
Data privacy laws allow individuals to exercise their rights, such as the right to be forgotten, and in certain circumstances, individuals may regain ownership of their data.
To retain data and maintain trust, companies need to be transparent by openly disclosing what data they collect, the purpose of the data collection, who the data processor is, etc.
7. The legal cornerstone: the GDPR
“I believe data protection to be one of the most important issues of the 21st century at all. We need a Bill of Rights for the digitale.”
- Tim Cook
7.1. The importance of the GDPR
The importance of the GDPR lies in its comprehensiveness, its impact on other data protection laws such as the CCPA in California, the LGPD in Brazil, the NDPR in Nigeria, and others.
The EU was the first to raise data protection legislation to this level and set an example to create a truly comprehensive, long-term framework in which organisations can take responsibility for how personal data should be processed.
The GDPR unifies data protection policies and laws throughout the EU and enforces them with heavy penalties.

Photo by Sora Shimazaki from Pexels
7.2. Why was GDPR necessary?
One of the reasons for the need for GDPR is the unprecedented technological advances that have taken place in the last few decades (only about 30 million people used the Internet in the mid-1990s), and the other is the tremendous increase in the amount of data that has accompanied technical advances.
„Over 2.5 quintillion bytes of data are created every single day, and it’s only going to grow from there. By 2020, it’s estimated that 1.7MB of data will be created every second for every person on earth.”
- Domo.com
This incomprehensible amount of data is at the heart of business and profit in many organisations and is collected and used in a way that was unthinkable a few years ago. And the way data is used also depends on whom it comes from: the user. The GDPR primarily protects data providers (data subjects): individuals who provide their personal information in exchange for using an online service.
Why? Because personal data does not belong to organisations, it needs to be protected. The GDPR was the first step in this direction, bringing a change of attitude between the user and the service provider regarding the use, management and handling of the data.

Image resource: VistaCreate by Igor Vetushko
7.3. What is the purpose of the GDPR?
The goal of GDPR is to protect personal data and give the individual back control over the use that companies make of their data. In particular, how their data is handled, what data is collected about them, who collects it and why. The GDPR gives the data subject a whole set of rights (GDPR Chapter 3 – Art 12-23).
The data subject’s rights are as follows:
- Right to be informed
- Right of access
- Right to rectification
- Right to be forgotten
- Right to restrict processing
- Right to data portability
- Right to object to processing
- Rights about automated decision making and profiling
The GDPR is designed to pave the way for Europe’s digital future, so it imposes huge fines to protect individuals’ data privacy, and violating GDPR rights can lead to huge fines.
As technology advances and the number of users increases rapidly, companies access, collect, store, and process more and more personal and sensitive data.
Nowadays, it is hazardous to ignore data privacy laws. In addition to being threatened with fines and lawsuits, the reputation of companies can be severely damaged, and their customers can quickly turn away from them. Compliance also protects companies and gives them a competitive advantage if they are rumoured to be very consistent with GDPR.
In order to comply with data protection principles, the right approach is to take proactive steps and measures, such as the introduction and continuous monitoring and development of appropriate data protection measures. It is also useful to implement and use data privacy software that helps you manage your data privacy program and automate your processes.
In addition to protecting individuals’ data, the GDPR legally obliges organisations to take full responsibility and accountability for how personal data is used, processed, and regulated by them.
7.4. Definitions of the major players of the GDPR
7.4.1. Data subject
Data Subject is a natural person who can be directly or indirectly identified through personal data (name, location, ID number, or other specific factors).
7.4.2. Data Controller
Data Controller is a legal entity, organisation, company, person, or institution that collects and processes personal data for predefined purposes. Data Controller is the one who determines the purpose of the processing and the means of processing.
7.4.3. Data Processor
Data Processor is a legal or natural person, organisation, or institution which processes personal data on behalf of the controller.
7.4.4. Data Protection Officer (DPO)
Data Protection Officer is responsible for supervising the implementation of the company’s data protection strategy and ensuring it is compliant with the GDPR and other applicable data protection laws.
7.4.5. Data Protection Authority (DPA)
Data Protection Authority or DPA (also known as Supervisory Authority (SA)) is responsible for monitoring the application of the GDPR and protecting the fundamental rights and freedoms of individuals (data subjects) related to the processing of personal data and process the complaints made by data subjects.
For further information, please check Art. 4 – GDPR Definitions.

Photo by Pixabay from Pexels
The development of information and communication technology has facilitated the involvement of third parties, communication between distant organisations and the implementation of organisational differentiation.
Due to third parties providing external services, customers’ personal data is transferred to more and more organisations during the implementation of a service, which complicates legal regulation, application, and compliance.
The issue is further complicated by the fact that with the spread of the Internet, we are using more and more globally provided services, the operators of which implement data processing from several countries. It is up to the data controller to decide whether to process the data within their own organisation or entrust this task to a data processor.
A data processor’s two most critical conceptual elements are entirely separate from the data controller and carry out the data processing on their behalf and instructions.

Photo by Fernando Arcos from Pexels
The identity of the data controller must always be examined in a specific legal relationship: the same person may be present in an infinite number of legal relationships, which can only be examined on a case-by-case basis to determine whether s/he is acting as a data controller or processor.
Under the Directive, to clarify the legal situation, the controller and the processor must enter into a contract that stipulates, among other things, that the processor may act only on the instructions of the controller.
In the case of cloud-based service providers, roles are often mixed, and data processors may qualify as data controllers for specific data.
8. The price of the violation of data privacy
”If you don’t protect your personal privacy, who will?”
- Unknown
Violation of GDPR rules is subject to very high penalties. This chapter reviews the penalties that companies can expect, their number and extent, and the highest fines to date.
8.1. The extent of GDPR fines
The GDPR entered into force on 24 May 2016 and was to apply from 25 May 2018 after a two-year grace period.
Art. 83 (4, 5, 6) of the GDPR sets out the level of fines and the factors affecting them. According to this, there are two levels of GDPR fines as follows:
· the lower level is up to €10 million, or 2% of the worldwide annual revenue from the previous year, whichever is higher
· the upper level is twice that size, or €20 million and 4% of the worldwide annual revenue.
8.2. Number and level of GDPR fines imposed so far
Since its application in 2018, 880 fines have been imposed, currently amounting to more than € 1.29 billion. Compared to 2020, both the number of GDPR fines imposed and the number of individual fines increased significantly in 2021.
According to Finbold, the total number of GDPR infringements increased by 113.5%, while the number of GDPR fines increased by 124.92% between July 2020 and July 2021.
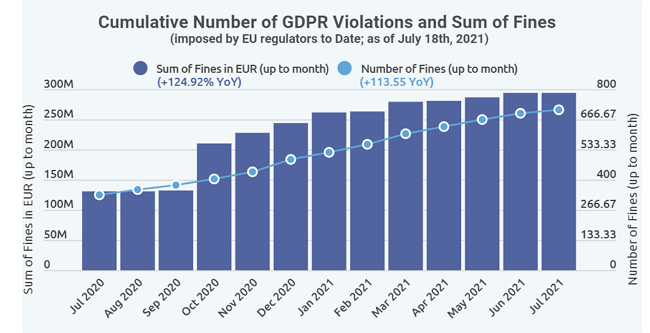
Source: Finbold (Finance in Bold) - Cumulative number of GDPR violations and sum of fines
8.3. The most significant GDPR fines ever
On 16 July 2021, the Luxembourg National Data Protection Commission (CNDP) imposed a record fine of € 746 million ($ 888 million) on Amazon Europe Core S.a.r.l. for breaching the GDPR due to non-compliance with general data protection principles. This was the largest fine ever received by a company for violating GDPR principles.
The second-largest fine was imposed on 2 September 2021 by the Irish Data Protection Commission (DPC). DPC has fined WhatsApp € 225 million for transparency violation.
The French National Commission for Informatics and Freedom (CNIL) imposed the third largest fine on 21 January 2019. The CNIL fined Google € 50 million for lack of transparency, inadequate information and personalisation of advertisements due to the lack of valid consent.
Fourth on the list is H&M (the Swedish retailer Hennes & Mauritz), fined € 35 million in 2020, and TIM (an Italian telecommunications operator) with a fine of € 27.8 million in 2020.
There are a lot of statistics on this on the Internet, for example, The biggest GDPR fines of 2019, 2020, and 2021 or 20 biggest GDPR fines so far (2019, 2020 & 2021). The graph below shows the top 10 penalties imposed so far for violating GDPR rules:
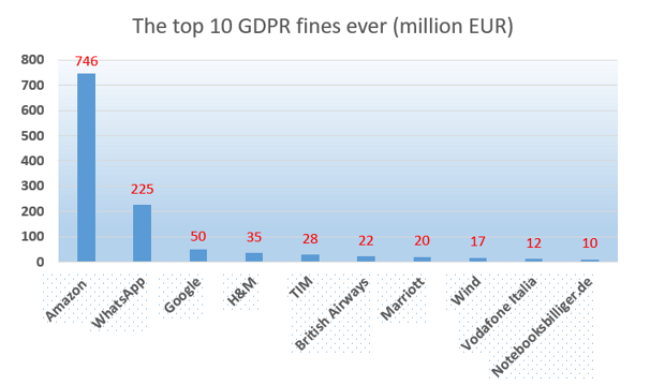
9. Data privacy trends
„Privacy is not for sale, and human rights should not be compromised out of fear or greed.”
- Pavel Durov
9.1. The rise of the regulations
As the rights of individuals to their data become more substantial, the need for regulation is becoming more and more apparent in the world, leading to more and more stringent data protection laws. Although the GDPR was not the first data privacy law, it paved the way for newer data security regulations. The California Consumer Privacy Act or the CCPA is also a data protection law modelled on the GDPR. It entered into force on 1 January 2020. In 2020, the Brazilian General Data Protection Law (LGPD) was introduced to protect about 140 million Internet users’ personal information.
9.2. Higher and more frequent fines, more awareness
Since the GDPR’s grace period has ended, more and more frequently and higher and higher penalties were imposed for violating the GDPR rules. These fines have made companies realise that they need to take the GDPR and its rules very seriously, so top management is increasingly inclined to set aside different sums of money to comply with such rules.
9.3. New roles and shifts in responsibilities
With the GDPR, new roles were introduced at companies: DPO (Data Protection Officer), CDO (Chief Data Officer), CISO (Chief Information Security Officer), to name some. With such new roles, new responsibilities and functions have also emerged.
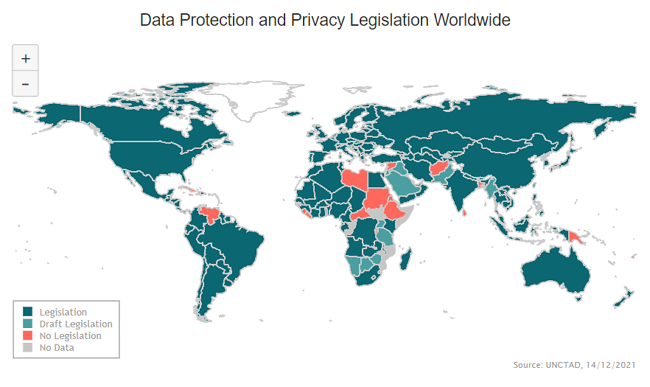
United Nations Conference on Trade and Development (UNCTAD): Data Protection and Privacy Legislation Worldwide
- 61 % of individuals active about their privacy are under 45 (DP Manager)
- 46% of customers feel they have lost control over their own data (Salesforce)
- 107 countries have set up laws to secure the protection of data and privacy (UNCTAD)
- 16% of countries are still without any data protection legislation (UNCTAD)
- 58% of European companies declared GDPR compliance as a top priority (IAPP)
- 97% of companies recognised competitive advantage from their privacy investments (CISCO Survey)
- Facebook owns 80% of the market share of social media platforms (ResearchGate)
- Google owns 90% of the market share of search engines (ResearchGate)
9.4. Data privacy officers are in great need
Adhering to the new legal conditions in terms of the workforce is an enormous challenge for companies.
Companies lack a considerable number of employees who would be able to act professionally in accordance with data protection legislation, establish procedures and automate existing ones. However, there is an urgent need for such highly trained professionals to comply with GDPR rules.
9.5. Transparency became key to success
Private users are becoming more aware of their rights to their data and are increasingly exercising their rights under the GDPR. In addition, they have more trust in companies that communicate openly with them, so the reputation of that company grows, which is obviously beneficial for the company as well.
Companies are also beginning to recognise this trend, as the GDPR has created a clean legal environment for users’ personal data.
10. Data privacy concerns about social networks
“I am a nonparticipant of social media. I’m not much attracted to anything that involves the willing forfeiture of privacy and the foregrounding of insignificance.”
- Billy Collins
Social networks are communication platforms that allow users to create a profile from their personal information and images to identify themselves, connect with other users and view their social networks.
With more than a billion users, Facebook is one of the world’s largest non-government data controllers. Its weight is determined not only by the number of registered users but also by the quantity and quality of the data they provide: from basic personal data (e.g. name, place and date of birth) to special data (e.g. religion, political views), which are provided voluntarily, increasing its credibility.
Through the acquaintances of the users, a very complex network of contacts can sometimes be drawn, which can often only be detected by intelligence tools and methods.
The dominance of Facebook is evident globally, but it should also be seen that more and more social sites are emerging (read the article: 101 Social Networking Sites You Need To Know About In 2021). Most of them are of English language or origin, but there are more and more others, like Mixi (Japanese), Qzone, RenRen and Weibo (Chinese) and Vkontakte (Russian).
The Vkontakte landing page reminds me a lot of the home screen of a well-known social site (Facebook):
The landing page of Vkontakte: is it the Russian Facebook?
In addition, users are changing: most newcomers come from a young age group, and their Internet habits are different: they typically no longer connect to social networking sites on their desktops or laptops, but they are online almost all day with their smartphones.
For a social network site, one of the ways to increase the number of users is to open up the possibility for users to register in more and more countries. However, new countries may have different legal systems, and it is challenging to provide an international service that works uniformly in all countries and complies with different legal systems.
Modern data protection legislation is becoming more and more stringent in more and more countries, mainly due to the data protection expectations and standards of the European Union.
In the case of social networking sites (e.g. Facebook, Twitter, Instagram) and content sharing services (Youtube, TikTok), the line is already blurred whether the user is only concerned or a data controller.
The social network provider qualifies as a data controller because it determines how and for what purposes personal data is processed. The service provider determines the type of data users can provide about themselves, the format and number of images they can upload and the settings on how they can share them. Defining the purpose of data management always entails the status of the data controller.

Image resource: VistaCreate by Igor Vetushko
Suppose natural persons process data exclusively for personal purposes. In that case, they are not subject to the obligations of a data controller (they upload pictures and other personal data about themselves in this case).
Users are increasingly using social networks for purposes that go beyond “personal use and purpose”. For example, if a user uses a social network site to recruit, engage, and promote members of organisations and associations, it is no longer considered personal use.
Social networks can also be easily used for “data mining”: users collect information about their friends (e.g. email, phone number) for personal or business use. If the user uses such data, for example, to organise a class reunion, it is still considered personal use. However, if the data of former classmates is used for business purposes or to send unsolicited emails for them, it already has an entirely different legal implication.
So if an individual uses the social network for economic purposes (product sales, marketing), she already has the status of a data controller.

Image resource: Photo by Firmbee.com on Unsplash
11. Turning personal information into profit
“Those who rule data will rule the entire world.”
- Masayoshi Son
Users’ personal data can be considered as the “oil of the Internet” since their knowledge and possession has a significant, lucrative value: although the use of the most important Internet services (e.g. Google, Facebook, Twitter, etc.) is free, yet they make a considerable profit from their users’ data and related advertisements. These companies need to know as much as possible about their users’ Internet habits in order to get the most targeted ads available for them.
Internet companies may collect data about their users on what they are doing, what information they are looking for, where they have logged in, and what device they used. This data makes it easier for companies to determine which ad is most likely to get the desired impact from users and then sell ad slots more expensively.
Horizontal and vertical data collection by Facebook is constantly increasing. In the case of horizontal data collection, Facebook can obtain the data of more and more users; one way is to acquire a user database together with the ownership of companies, for example, in the case of WhatsApp and Instagram.
”Privacy is dead, and social media hold the smoking gun.” – Pete Cashmore.

Image resource: Glen Carrie on Unsplash
In the case of vertical data collection, Facebook finds out more and more information about each person involved, mainly through a combination of available data. For example, based on uploaded scuba diving images, that person is bombarded with related ads.
Facebook tailors feeds and ads based on increasingly advanced algorithms to meet its users’ needs. Most companies that provide online services do everything they can to gather as much information as possible about their users. How much data a page can obtain depends primarily on the time users spend on the page, the type of page (how interactive the content is), and how much and what kind of information the users need to provide to use the service.
News sites generally do not require any registration, and users can browse them at any time. But even in this case, they can get a lot of information about the visitor: from where and what kind of device they logged in, whether they have been to the site before, what their interests are (what links they clicked on), etc.
The next step is when the user has to register on a site to use its features. During registration, the user provides some personal information: age, place of residence, possibly education or interests. After accepting the data privacy statement, the user will usually be offered the opportunity to subscribe to a newsletter as an option.
Facebook and other social networking sites have taken the scope of the information collected to a new level: in addition to the basic personal data provided voluntarily, they can get a complete picture of the user, as users often provide their schools, workplaces and areas of interest voluntarily.
With tremendous amounts of data and the ability of the largest web companies (e.g. Facebook, Google, Yahoo) to directly reach their user groups based on special features (e.g. women between the ages of 20 and 30 who live in Bristol and are interested in fashion) bring an unbeatable advantage over traditional advertising spaces (e.g. TV, radio, newspapers, posters) and completely change the market structure that has developed so far: the amount spent on advertising is increasingly being reallocated to online advertising spaces.

Photo by Adem AY on Unsplash
Another trend is that databases are concentrated in the hands of the largest companies: large companies like Microsoft are constantly buying smaller web companies and receiving all users’ personal information (often, the database is the only reason to buy).
The working principle of behavioural advertising
In the case of online behavioural advertising, the service provider monitors the user’s Internet habits and, in conjunction with their personal data, organises them into interest groups (such as those interested in travel, cars or clothing) and then shows the groups advertisements according to their interests.
The working principle of behavioural advertising is that the service provider stores the type of pages their users have visited on the users’ device in a cookie. The stored data show which pages the users have visited, and from these data, it can be deduced what products and services they would buy.
12. Personal data as an object of sale
“Data is the most valuable asset in the world.”
- Brittany Kaiser
Since companies nowadays often acquire other companies because of their user database (e.g., Facebook acquired Whatsapp, Microsoft acquired Skype), the level of protection of personal information must not be reduced. Adherence to data privacy policies is vital when acquiring companies, as the identity of the data controller or owner may change.

Photo by Tushar Mahajan on Unsplash 650
One of the most critical questions is whether the scope of the statements of consent given to the former controller extends to data processing following a “change of ownership”.
In recent decades, massive systematised electronically recorded personal data has changed hands during companies’ sales, mergers, divisions, and reorganisation. It is imperative for companies to ‘own’ their users’ personal data, which can be easily converted into profit for them.
The data controller’s identity does not change in theory in the case of a company acquisition, but in practice, it does. Although the same company remains responsible for personal data, the new owner manages and determines its strategy. In the event of a change of ownership, the method and purpose of data management may also change, of which the customers must be informed.
13. Data privacy regulations worldwide
“We’re entering a new world in which data may be more important than software.”
- Tim O’Reilly
Technology and the way data is communicated, shared and managed have also changed a lot over the last few years, requiring the development of a new, comprehensive legal framework.
The GDPR was the first serious intention to curb the excessive use of personal data and to impose appropriate fines on data processors and data controllers. More importantly, the GDPR empowered data subjects to regain control of their data privacy.
Privacy law predictions
But GDPR is not the only data protection law. Others followed it, including Brazil’s General Personal Data Protection Law (LGPD) and the California Consumer Privacy Act (CCPA). Other data privacy laws will likely emerge in the future, as the same problems will have to be remedied in other parts of the world with such legislation. According to Gartner, by the end of 2023, modern data protection laws will cover the personal information of 75% of the world’s population.

Image resource: VistaCreate by Andrew Lozovyi
In the world of the Internet, companies’ customers can come from all over the world, and due to the increasing number of data protection laws, companies have to deal with more data protection laws in different jurisdictions.
This also means that companies will most likely have to employ professionals who specialise in data protection and help them understand and comply with the sometimes different data protection laws. In addition, companies will have to strive to automate their data protection systems. In the EU, GDPR directives apply, but they will have to be adapted to the jurisdictions of other countries.
Organisations need to consider this when developing their business plans, strategies, and marketing activities not only because of the fines they might face but also because individuals expect this.
Benefits from aligning with data protection laws
The percentage of organisations claiming to reap significant business benefits from data protection has grown from 40% in 2019 to more than 70% by 2020. The benefits depend on operational efficiency, agility, innovation, investor attractiveness and brand value.
Data protection software
Data protection software can help you achieve compliance by automating and simplifying your data privacy policies. The data protection software monitors statutory deadlines at the request of each individual involved and helps them better understand their customers.
Data protection laws allow individuals to exercise their rights, such as the right to be forgotten, and in certain circumstances, individuals may regain ownership of their data.
For companies to retain data and maintain trust (and their customers!), they need to be transparent by openly disclosing what data is being collected, for what purpose, who is processing the data, etc.
A data leak can have a devastating effect on a company’s reputation and may cause a much more significant financial loss than technical damage itself. Encryption is among the essential tools for managing the risk of a data breach. It is a critical tool for protecting sensitive data, including personally identifiable information (consider the link with GDPR), that can be used for identity theft.
Learn more about how devastating a data leak can be (The Worst Data Breaches of 2021)and how encryption can help minimise the risk (Encryption: the unnoticed law enforcement force in cyberspace).
14. European Data Protection Day
“The Internet is a worldwide platform for sharing information. It is a community of common interests. No country is immune to such global challenges as cybercrime, hacking, and invasion of privacy.”
- Lu Wei
On 26 April 2006, the Council of Europe decided to launch the European Data Protection Day. This prominent event is celebrated every year on 28 January. This is a symbolic date: it is the anniversary of the opening for signature of Council of Europe Convention 108 for the Protection of Individuals concerning Automatic Processing of Personal Data.
The Convention 108 celebrated its 40th anniversary on 28 January 2021. Its modernised version named Convention 108 + was published in 2018.
Source: - 40th anniversary of the Council of Europe Convention 108 on data protection
Data Protection Day (also known as ‘Data Privacy Day’ outside of Europe) is an international event currently observed in the United States, Canada, Israel, and 47 European countries.
On the ‘National information’ page of the Council of Europe, you may check which countries are parties, non-parties or observers to Convention 108. Data Protection Day aims to raise awareness and promote data privacy and data protection best practices.
The purpose of the Data Protection Day is also to allow European citizens to understand why and what personal data is collected and processed about them and what rights they have about their data processing. This event is to inform and educate the public about their day-to-day rights. However, it can also provide an opportunity for the public to meet data protection professionals and ask data protection-related questions.
Participants may also be made aware of the risks inherent in and associated with the unauthorised misuse and unfair handling of their personal data.
15. Data protection and privacy in Luxembourg
“Luxembourg is among the best performers in terms of data protection, in particular thanks to the culture of confidentiality that has been built around the financial centre. This culture has facilitated the adoption of new measures to protect personal data.”
– Stephane Omnes DPO of 2020
15.1. Data protection laws in Luxembourg
Data protection in Luxembourg is primarily governed by the GDPR (Regulation (EU) 2016/679). On 1 August 2018, Luxembourg adopted two new data protection laws implementing the GDPR: The Data Protection Act and the Data Protection in Criminal Matters Act.
The Data Protection Act provides specific requirements or exceptions concerning the processing of personal data. In contrast, the Data Protection in Criminal Matters Act relates explicitly to protecting individuals about the processing of personal data in criminal matters and for the processing of national security. The links to both acts can be found on the website of CNPD.
In this article, this topic is almost only mentioned, as it is much more diverse than this and, for reasons of length, it is not possible to discuss it in more detail here. However, you may read the articles Luxembourg - Data Protection Overview, Data protection laws of the world – Luxembourg, and Data protection and cybersecurity laws in Luxembourg for further information.
15.2. Data Privacy Day in Luxembourg
The Data Privacy Day, organised by the Restena Foundation and the University of Luxembourg, is an annual event for people interested in data privacy protection. The aim is to raise awareness and promote best practices in this area at the European and international levels.
The programme for 2021 (Data Privacy Day – Take control of your privacy) is on the website of CNPD. January 28, 2022, is approaching with more programmes.
Besides this event on a national level, CNPD also organises international events and conferences. The Global Privacy Assembly (GPA) was launched in November 2019 (formerly named the International Conference of Data Protection Commissioners). It is a forum for a global exchange of views where 130 members can share the best data protection practices.
16. How can SECURITYMADEIN.LU help?
„Paying with your data for “free’’ services is much more expensive that most people realize.”
- Mat Travizano
16.1. SECURITYMADEIN.LU
SECURITYMADEIN.LU is the cybersecurity agency for the Luxembourg economy and municipalities. It provides extensive cybersecurity expertise and solutions to SMEs and companies of all sizes and municipalities through its three departments: CIRCL, CASES and C3, in close collaboration with the CYBERSECURITY Luxembourg ecosystem’s players.
16.2. CASES
CASES (Cyberworld Awareness Security Enhancement Services) is part of SECURITYMADEIN.LU. It has multiple services available for the public to raise awareness concerning cybersecurity.
Fit4Contract is a self-assessment tool made for helping clients in reviewing their contracts with their suppliers. It is similar to Fit4Cybersecurity but is built to help the user identify cybersecurity and data privacy concerns to negotiate supplier contracts. Fit4Contracts is your assistant in information security concerns when working with external suppliers.
CASES has developed in consultation with CNPD its newest product, Fit4Privacy. It is a self-assessment tool (a questionnaire consisting of 17 questions) to help organisations assess to what extent they control their personal data risks. It is free and is available in three languages: English, French, and German.
16.3. CIRCL
The Computer Incident Response Center Luxembourg (CIRCL) is also part of SECURITYMADEIN.LU, with the initiative to gather, review, report and respond to computer security threats and incidents.
Information leak analysis (AIL framework) is one of CIRCL’s services. AIL is a modular framework and a powerful tool to analyse potential information leaks from unstructured data sources like pastes or social networks or unstructured data streams.
In the video below, Alexandre Dulaunoy explains the mission of CIRCL in analysing, collecting and handling the data by AIL and how data acquired during a breach is becoming a product used and sold by cybercriminals.
Cybersecurity Breakfast #41 - Data Breach: The Good, the Bad and the Ugly
The primary aim of the framework is to gather credentials, emails, credit card numbers, and so on to help security experts detect leaks and then react accordingly. AIL enables researchers and investigators to uncover malware in massive amounts of data.
AIL can be extended to support other functionalities to mine sensitive information. You may check the list of reported detected information leaks in Luxembourg.
17. Conclusions
„If we don’t act now to safeguard our privacy, we could all become victims of identity theft.”
- Bill Nelson
The emphasis has shifted from industrial production to service provision in recent decades, increasing the overall value of information and the importance of managing it responsibly.
As technology advances and the Internet spreads, companies collect, store, and process more and more personal data. Today, no company can afford to ignore or unpreparedly handle data privacy laws. Companies are threatened with severe fines and lawsuits, and their reputation and customer loyalty are continuously tested.
- Perform an information audit to determine what information you are processing and who can access it
- Provide clear information on data processing in your data privacy policy
- Take data protection into account at all times in your processes
- Encrypt, anonymise or pseudonymise personal data whenever possible
- Establish an internal security policy and increase privacy awareness
- Create a procedure for notifying authorities and data subjects in the event of a data protection incident
- Make it easy for your customers to exercise their privacy rights whenever they want
The right approach is to take proactive steps and actions, such as implementing appropriate data privacy measures or data protection software that helps companies manage their data privacy program and automate their processes.
Once it happened, the data protection incident shall be reported by the controller to the competent data protection authority without delay and, if possible, no later than 72 hours after becoming aware of it (unless the data protection incident is not likely to endanger the rights and freedoms of natural persons).
Suppose the data protection incident is likely to pose a high risk to the rights and freedoms of natural persons (for example, large-scale leakage and disclosure of customer data). In that case, the data controller shall inform the data subject of the data protection incident.
Besides the technical deficiencies, the human side of any organisation may as well pose a severe security risk if employees do not become familiar with that organisation’s data management practices and if they do not have sufficient knowledge of data security measures. That is why it is essential that employees receive adequate training from the outset of their employment and know whom to turn to with their data protection and security issues.
However, the controller or processor should also verify in practice that the employees involved in data management have acquired the necessary knowledge in the event of a change in circumstances or, if necessary, provide further training for staff involved in data management.

Photo by AbsolutVision on Unsplash
It comes from the above that both the controller and the organisations acting as processors have to meet very nuanced and multifaceted requirements to guarantee an adequate level of data security and to determine with due care the nature and characteristics of data processing and the risks involved in the applicable data security measures.
In addition to enjoying the benefits of the explosive technological advancement, we also need to pay close attention to maintaining our freedom of choice and control over our personal information.
Today, data protection and data privacy are no longer just legal requirements but crucial for trust in rights and freedoms in today’s information society.
Finding the right balance between the advances in technology and the ever-evolving challenges of data protection and data privacy is one of the biggest questions of the present and the future…

