- 10 Feb, 2022
- Topic of the Month

This article was initially published on 03/01/2021 and revised on 10/02/2022.
1. Introduction & Definition
‘The Internet is no longer a web that we connect to. Instead, it’s a computerized, networked, and interconnected world that we live in. This is the future, and what we’re calling the Internet of Things.’ — Bruce Schneier
The Internet of Things (IoT) is transforming our physical world into a system of complex and dynamic connected devices of unprecedented size. But what is IoT? How can we define it?
We do not use the term ‘IoT’ for only one thing and that is what it makes often unclear what we mean by that. Sometimes we mean by it the physical devices, systems that are in a network, communicating with each other; other times we refer to the system itself.
This way or the other, it is something non-tangible, abstract, something that has been happening around us and will definitely change our lives whether we want it or not.
Connected objects have gradually invaded our daily life. The IoT brings together all the sensors and objects connected to the Internet, thus allowing remote control of our physical environment. Among the new technological trends, IoT increasingly plays a predominant role.
Just like the term ‘artificial intelligence,’ the IoT acronym is used in abundance. XR (Extended Reality), ML (Machine Learning), DevOps (Development and Operations), IoT (Internet of Things), VUI (Voice-as-User Interface), SaaS (Software as a Service) … and the list is growing. These are among the most used (and sometimes overused) IT & Technology buzzwords you can hear nowadays. But do we know what exactly these are, or can we define them?
If you Google them, many of the answers are unnecessarily technical. For instance, if you search for the term ‘IoT definition,’ you will get the explanation below: ‘The Internet of Things (IoT) refers to a system of interrelated, Internet-connected objects that are able to collect and transfer data over a wireless network without human intervention. The personal or business possibilities are endless.’
So, after this first search, you do another one, and most probably you get another technical description. This way or the other, all definitions boil down to the notion that IoT is when you connect things to the Internet and make these things able to communicate with each other without further human involvement: IoT is a network of connected devices.
Generally, connected objects are associated with the daily uses of the general public, such as smartphones, connected bracelets, connected watches, household appliances, etc. Connected homes are also at the heart of the IoT topic. More commonly known as home automation, the connected home has become a predominant trend.
This new reality gives rise to particular risks. These ever-increasing interconnections are potential security holes, and the large amounts of data processed and stored in the cloud are a target for some criminals.
The Internet of Things (IoT) poses a significant risk to the entire digital ecosystem. This is because many devices are designed without built-in security systems that provide protection against hackers. This article provides an overview of issues and challenges related to this technology through the prism of information security.
2. The history of IoT
‘As the Internet of Things advances, the very notion of clear dividing line between reality and virtual reality becomes blurred, sometimes in creative ways.’ — Geoff Mulgan
IoT, as we see it today, has not been around for very long. The Internet itself, as the backbone of IoT, started in 1962 as part of DARPA (Defense Advanced Research Projects Agency), which later evolved into ARPANET. Yet, it only happened in the 1980s when commercial Internet providers opened the way to the creation of the network we call ‘Internet’ today.
The first ‘smart’ device was a Coca-Cola vending machine – also in the 1980s –, but at this time no one used the term ‘smart’ or ‘IoT’. Maybe we can thank the birth of IoT for the laziness of the local programmers at the Carnegie Melon University (Pittsburgh, Pennsylvania) who connected by the Internet to the above-mentioned vending machine to check and see if there was a drink available and whether the drink was cold, before walking there.

Source: The reimagination thought Leaders summit, Sydney, 17 Nov 2015 KEVIN ASHTON
It happened only in 1999, when Kevin Ashton, the Executive Director of Auto-ID Labs at MIT, used the term ‘Internet of Things’ first during his speech while he was making a presentation for Procter & Gamble:
‘Today computers, and, therefore, the Internet, is almost wholly dependent on human beings for information. Nearly all of the roughly 50 petabytes (a petabyte is 1,024 terabytes) of data available on the Internet were first captured and created by human beings by typing, pressing a record button, taking a digital picture or scanning a bar code…
The problem is, people have limited time, attention, and accuracy. All of which means they are not very good at capturing data about things in the real world. If we had computers that knew everything there was to know about things, using data they gathered without any help from us, we would be able to track and count everything and greatly reduce waste, loss and cost.
We would know when things needed replacing, repairing or recalling and whether they were fresh or past their best.’
… and the rest is history.
3. Looking ahead: Top IoT trends
‘There will be all kinds of hiccups, horror stories, accidents, deliberate acts of sabotage and other bumps along the road that will slow but not stop our greater connectivity. Convenience and empowerment always seem to win for most people, even at some loss of privacy, control or transparency.’ — Scott McLeod
Edge Computing
Data processing at the edge of a network will likely continue to grow in importance. Edge computing makes it possible for data to be accessed and analysed in near real-time. As the number of connected devices increases exponentially, just like data produced by them, it will become crucial to be able to handle and analyse data as quickly as possible.
Digital Twins
Digital twins are virtual representations of a process or system that work in the same way as their real-life counterparts. Displaying all data points of connected sensors in digital twin format provides a more holistic picture of physical object performance.
Predictive Maintenance
Many organisations adopted planned maintenance of equipment and did not wait for incidents or malfunctions to happen. Instead of reactive maintenance (as a response to a failure or malfunction), many companies will use predictive maintenance that utilises data gathered from control systems and connected sensors.
Remote Operations
In response to the COVID-19 pandemic, previously unconnected assets have been connected to enable remote operations. It is predicted that in the future we will see growth in the adoption of IoT.
Advanced Data Analytics
The real benefit of IoT comes not only from the data but from the analytics that generates useful insights and helps businesses make smart and informed decisions. As the amount of data generated increases, analysis becomes increasingly important. Artificial intelligence and machine learning will play an ever-important role in this process.
Next Generation IoT
Nowadays 80% of data processing and analysis takes place in data centres and 20% in intelligent connected objects. Over the next 5 years, 75% or more of data processing and analysis is expected to run at the edge of the network.
Given the inevitable fact that 75% of the European cloud market is dominated by non-EU players, Europe has no choice but to take advantage of the trend towards the new Internet of Things (IoT) and edge computing skills.
Edge computing is changing the way we perceive, analyze, and control our environment. It will also impact the cloud, AI, manufacturing, data centres, electric mobility and autonomous vehicles.
The Next Generation of Things (NGIoT) has published a roadmap (The roadmap for IoT research, innovation and deployment priorities in Europe 2021-2027) with projections and priorities for research and deployment of IoT and cutting-edge computing across Europe from 2021 to 2027.
The roadmap outlines comprehensive IoT research and innovation aspects, summarizing the results of stakeholders such as the Next Generation IoT and Edge Computing Strategy Forum and the Digital Autonomy in the Computing Continuum.
The roadmap covers a very wide range of IoT issues and outlines ideas and plans for more efficient and secure use of IoT in the future. It also presents the final recommendations of the IoT research, innovation and deployment priorities. The following figure shows the areas covered in the roadmap:

Major topics in the IoT Roadmap for Research, Innovation and Deployment Priorities
4. How big is IoT?
- There are more than 50 billion IoT devices as of 2020 (from 8.7 billion in 2012)
- These devices will generate 4.4 zettabytes of data this year (a zettabyte is a trillion gigabytes)
- The IoT market size in Europe estimated to reach €242,222 million by the end of 2020
- The value of the IoT market in 2025 will be around $14.4 trillion
- The annual revenue from IoT sales is forecast to hit $1.6 trillion by 2025
‘The Internet will disappear. There will be so many IP addresses, so many devices, sensors, things that you are wearing, things that you are interacting with, that you won’t even sense it. It will be part of your presence all the time. Imagine you walk into a room, and the room is dynamic. And with your permission and all of that, you are interacting with the things going on in the room.’ — Eric Schmidt
The growth of the Internet of Things in terms of the number of devices, data produced, and revenue generated have been stunning: there are more than 50 billion IoT devices as of 2020 (from 8.7 billion in 2012), and those devices will generate 4.4 zettabytes of data this year (a zettabyte is a trillion gigabytes).
If, in addition to the number of assets or annual revenue, market size is also considered, we may say that the IoT market size in Europe is estimated to reach €242,222 million by the end of 2020.
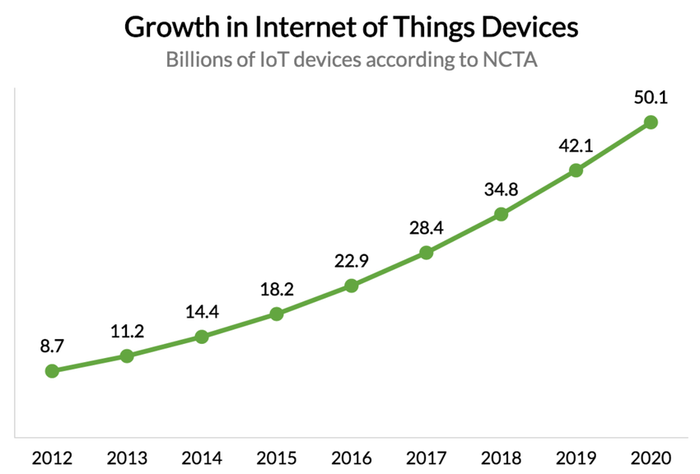
The number of IoT devices is growing exponentially and is estimated at 75.44 billion by 2025. As the number of installed IoT devices increases, market share will increase by $ 4 trillion by 2025.
5. Smart Solutions
‘Internet of Things is changing and transforming everything from business to life. Imaginations are boundless and opportunities are infinite. Everything is being wired up or connected wirelessly – architecture, energy efficient sensing, secure networks, quality of service, new protocols, participatory sensing, data mining, GIS-based visualization, cloud computing, and international activities. It simply means that powerful information will be at our fingertips.’ — Mehul Nayak
Out of the myriad smart solutions, five are outlined in this chapter: smart phones, smart offices, smart homes, smart wearables, and smart toys. These belong to the so-called ‘Consumer IoT’ or, even shorter, CIoT. Consumer IoT refers to the Internet of Things in the context of consumer applications, use cases and devices.
5.1 Smart Phones
Smartphones are computers with functionalities comparable to that of a ‘real’ computer. They have the same weak points as computers, but their portable format carries additional risks (loss, theft, unsecured connections). They can also be used for malicious purposes (network spoofing, invasion of privacy, misuse of images, etc.).
Also, smartphones are very often the first point of contact for connected objects and make it possible in particular to control them or simply exchange data with them.
Smartphone security is therefore essential if we want to ensure the security of the connected objects that revolve around them. Conversely, compromised connected objects could in turn infect smartphones. Smartphones can also help us control our connected objects, and to secure them or find them in the event of a loss.
In short, connected objects, smartphones and cloud services go hand in hand and we must ensure the safety of each of them to prevent problems from quickly spreading to the whole.
5.2 Smart Offices
The Smart Office is a rapidly evolving concept. It consists of integrating technologies into work environments, in order to facilitate a series of common tasks in the daily organisation of work. The goal is to gain flexibility and productivity and allow employees to focus on their essential tasks.
Beacons, sensors, and mobile applications constitute the basic building blocks of the Smart Office which make it possible to streamline or even automate a large number of processes.
Example: a connected coffee machine allows you to better manage its operation as well as the coffee supply, but be careful: a coffee machine can pose risks to your privacy and the security of your data.
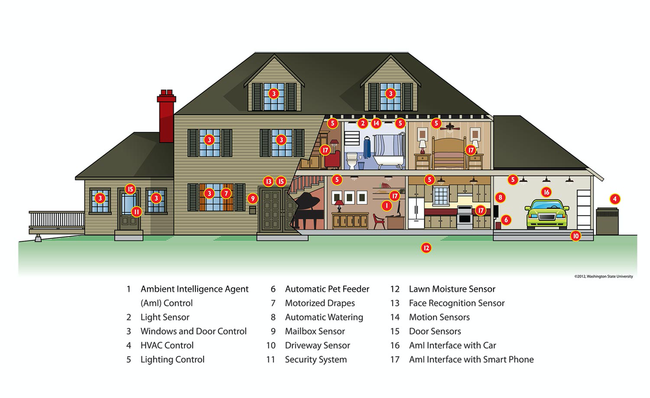
5.3 Smart Homes
With the help of sensors and information technology, users can control their homes from a distance. Improved quality of life, reduced operating costs and increased home security are just a few advantages of smart home solutions.
Whether you spontaneously leave work early and turn on the heating from your desk, forget what is left in the fridge when you get to the supermarket and look at your smartphone for a glimpse, or just want to make sure you have the hob switched off on holiday – the Smart Home makes all this and more possible.
The number of smart devices used in our homes is growing exponentially, often creating a complex, barely transparent, difficult-to-manage system:
You may use Keymitt’s Smart Lock and Wi-Fi Hub together to lock or unlock your door from wherever you are by using your smartphone.
By using Keymitt’s Smart Lock, you can remotely check whether a door is locked or not. Also, you may open it remotely if it is needed (think about how much this offers for Airbnb rentals, for example, as this provides another layer to automate their business securely).
Alternatively, you may use the Keymitt Push to physically push a button at your home with a single click on your smartphone. The basic idea behind any similar product is that you do not have to be physically there, you can make the change remotely.
With Smart Cube’s solutions, you may integrate your devices (Alexa, Sonos, smart TV, etc.) and create a smart home solution.
The DOVIT smart home integrated system alarms you in case of an intrusion attempt, water- or gas leak, fire, etc. It also provides video surveillance, anti-intrusion solutions, presence simulation, and deterrence services. Besides the immediate notification, thanks to the connected surveillance system, you may check and see in real-time what is happening at your home.
ModernHome uses two standards (KNX and Z-Wave) to provide keyless entry, lighting control, smart air conditioning with automated windows and blinds, and of course, an integrated smart home security module.
Besides the above companies that specialised in IoT in Luxembourg, there are many more, for example, EnOcean, Signify, Sigfox, RMS, POST Télécom, etc.
There are many companies in the market offering IoT-related services. The nature of the service may vary, so you may want to contact different companies for more information. Security cameras allow you to remotely monitor your interior and detect a potential intrusion. But some poorly secured models invite voyeurs and hackers to your home with bewildering ease of access.
5.4 Smart Wearables
Smart Wearables, also called simply ‘Wearables,’ whose name is derived from the English term ‘Wearable Computing Device,’ are small computer systems that can be worn directly on the body. Wearables belong to the category of ‘smart devices’ because they can be networked with other devices via the Internet or other data transmission technologies.
The most popular wearables are
- Fitness or Activity Trackers
- Smart Watches, which generally combine the applications of a Fitness Tracker and other functions
- Smart Headsets (smart headphones)
- Smart clothes and glasses are less common
In order for wearables to be able to offer their functions, personal data is collected through corresponding applications.
5.5 Smart Toys
The toy industry has also embraced the IoT. There are now ‘smart’ dolls, interactive tablets, drones that can be controlled via the Internet or even connected soft toys. The connected toy is a hybrid creature that sits between the toy and the communication tool. With a direct or indirect connection to the Internet, it is much more than an electronic game. It is a communicative object intended for young audiences.
Most connected toys have interactive functions: they can ask or answer questions and even lead fun activities. Children can, therefore, interact with the toy almost autonomously.
6. Protect and Prevent: Security challenges for IoT
‘… purchasing 10-20 different services from 10-20 different vendors using 10-20 different apps with 10-20 different user interfaces. If that’s the way Internet of Things goes, it will be a long tough slog to Nirvana.’ – Bob Harden
Smartwatches, smart coolers, smart light switches. They make our lives easier in many areas – but also the things of the attackers.
The proliferation of connected devices and their growing interconnection generate an increasing amount of data that is transmitted between devices and then over the Internet. This greatly increases the risk of security vulnerabilities being exploited. An IoT system is like a chain with a level of security that matches the strength of the weakest link in the chain.
The most common concern of manufacturers and users (commercial entities, administrations or private individuals) alike is undoubtedly that confidential or private data will fall into the hands of cybercriminals, competitors or simply the general public.
The use of connected devices and the continuous and abundant collection of data only increase the possibilities for malicious actors to find vulnerabilities. Above all, remote maintenance access that allows full control over the devices is an attractive target for cybercriminals.
We must also be wary of certain interfaces or technologies, such as Bluetooth, that are vulnerable by design. They can be easily compromised and lead to information leaks.
As the number of connected devices increases, so does the cybersecurity concerns associated with their implementation and use. If we draw a parallel between the number of devices and the frequency of the threats associated with them, it is easy to see that we are in big trouble. But what are the factors that need special attention? This chapter tries to summarise these.
A Multitude of Exploits and Bugs
As technology advances, the number of security incidents explodes. There are billions of devices in the market for millions of manufacturers, which are enthusiastically struck by hackers with different levels of knowledge. Although manufacturers try to constantly improve and patch the firmware of their devices, drivers for abuse usually go several steps ahead of them.
Malware Hotbeds
Digital criminals prefer to infect various malicious software on IoT devices. Poorly protected IoT devices can be taken over by hackers who control them in order to use them for synchronised and targeted DoS attacks. In case attackers manage to take control of a large number of IoT devices, they can create a ‘robot network’ (Botnet). These botnets pose a significant threat: these are made up of a plethora of infected devices and are designed to perform tasks (overload attacks, DDoS) that require heavy computing capacity.
Smart devices are excellent targets because they often have a lower priority for users than computers. It is clear to us that computers – for instance – need to be protected, but many of us do not think about the tiny devices hidden in the background.
Ill-considered factory loopholes
One of the main problems with some tech companies building IoT devices is that sometimes they are too careless when it comes to the handling of device-related security risks.
Lack, rarity, the imperfection of updates
Most of the IoT devices do not get enough updates, while some do not at all. This means that a device that was once thought to be secure when customers first purchased it is insecure and may be prone to hackers and other security issues.
Also, some manufacturers offer firmware updates only for a short period of time, which leaves their customers exposed to potential attacks as a result of outdated hardware and software.
Leaving default passwords unchanged
The Mirai botnet, which caused probably the most disruptive DDoS attack is perhaps one of the best examples of the issues that come with shipping devices with default passwords and not telling consumers to change them as soon as they receive them.
Weak credentials and login details leave IoT devices vulnerable to password hacking and brute-forcing in particular. Manufacturers should alert their customers to the need for a password change, but it is also the customer’s responsibility and interest to change the default password as soon as possible after purchase.
Data Protection and Legal Risks
Given the amount of data generated by IoT devices, it is no wonder that data privacy and security are among the major concerns about IoT adoption. Once devices are connected to the Internet, they become vulnerable to possible security breaches in the form of hacking, phishing, etc.
The usage of IoT devices can raise ethical, legal, and social risks we face in relation to the ever-expanding IoT services. Previously, it was not necessary to pay special attention to the protection of our non-literal personal data, i.e. our location, our current physical or mental health, or even the protection of our future travel plans.
Even in the not too distant past, due to the lack of technology, data could either not be stored digitally (location data) or the data subject could specifically identify the data controller person or organisation (health data).
IoT devices, especially wearable ones (smartwatches, glasses, but even smartphones) are by their nature constantly on, constantly detecting, collecting and sending data and communicating. In practice, this highly sensitive personal data is completely devoid of notifying and informing the user who will be the controller of the data, what the purpose of the data processing will be, how long the storage will last and whether any information will be passed on to third parties.
For larger manufacturers, the most common solution in the wearable device market is to use the screen of a mobile phone application needed to operate our sports bracelet, which stores and analyses our sports activities and movement data, to inform the user and obtain consent.
However, continuing with current data protection practices, users may increasingly be deprived of data management information due to the shrinking size of products, which simply results in them becoming too small to have a display. It can therefore be seen that, due to the nature of IoT devices and the speed of technical development, traditional legal frameworks such as the precise definition of the controller and the purpose of data management or specific, informed and clear consent cannot follow the innovation driven by Internet-based sensor objects wave.
Danger of Obsolescence
Due to the planned obsolescence, our household appliances such as a washing machine or dishwasher need to be replaced every couple of years. The speed of technological development always offers better or smarter devices, so we buy new and more modern gadgets every few years. Consequently, not only will we spend more, but we will also be burdening the environment with a lot of waste.
Constantly Bombarded with Advertisements
Where there is a display, there is also advertising. By browsing the Internet, you frequently run into advertisements. It will not be any different with IoT, in fact, it will only get worse: your fridge will offer you a chain store when it comes to food, your smartwatch will tell you which fitness app to buy. Using the data collected about us, we will receive personalised advertisements and offers. Our tools will get to know us, so they will simply bombard us with ads.
The moment will come when our smart bracelet will send info to our smart refrigerator ‘saying’ that we have put on some weight and instruct the cooler to display diet advertisements and low-calorie recipes rubbed under our noses every moment that we ate two cookies.
Digital addiction and dependence
All devices around us become more and more intelligent each day. Machines think, help, respond to us, and we rely more and more on them.
Many people panic if they forget their smartphone or smart bracelet at home: who will tell them how many steps they have taken, how many calories they have consumed, have their favourite team won or lost the last match, etc.
As long as we can control these devices, as long as they do what they are programmed for, things are fine. The question is when the moment will come when machines will rise…
7. Protect and Prevent: Are we destined to an unhappy end or is there still hope?
‘The thing that keeps me awake at night – and should keep a lot of CEOs awake at night – is the disruptive impact of the Internet of things and connected devices.’ — Cherie Fuzzell
This chapter focuses on what we can do to protect our devices (and so ourselves) from cyberattacks.
- Password Change: The first precaution to take is to ensure a high level of password complexity.
- Physical Security: Connected objects are small in size and easy to move; therefore, they must be protected against the risk of theft, sabotage or compromise by a malicious third party.
- Frequent Updates: It is particularly important to exclusively use patches provided by the respective suppliers.
- Purchase Devices Only from Reliable Manufacturers: Choose devices from well-known companies that have a reputation to lose.
- Network Inventory: Identify and know the properties of your IoT products that you are going to integrate into your computer network.
- Deactivate/remove non-used devices from your network: Deactivate any device that is not in use.
Password Change
The first precaution to take is to ensure a high level of password complexity. These must contain a mixture of upper – and lower-case letters, numbers and special characters. When first accessing the configuration settings of the IoT device, it is advisable to create your own administrator account and delete all default accounts. This way, attacks on these easy targets can be prevented.
Physical Security
Connected objects are small in size and easy to move; therefore, they must be protected against the risk of theft, sabotage or compromise by a malicious third party. One of the first actions is to remove or deactivate all types of interfaces that are not necessary for the proper functioning of the connected device (e.g. a USB interface, superfluous wireless connections). In some cases, it is advised to physically secure the device or protect it with an additional structure.
Frequent Updates
It is particularly important to exclusively use patches provided by the respective suppliers. This is especially important for connected objects which are – by definition – permanently exposed to potential attacks.
If regular and automatic updates can be activated, it is strongly recommended to activate them. In the absence of an automatic update feature, it is strongly recommended that you regularly check to see if updates are available. Software updates minimise the likelihood of being attacked via known vulnerabilities as each update fixes known issues.
Purchase Devices Only from Reliable Manufacturers
Choose devices from well-known companies that have a reputation to lose. It is strongly advised to avoid using cheap products from unknown manufacturers. In general, manufacturing costs are kept low by simply assembling low-quality components that are often technically out of date and that do not include state-of-the-art security mechanisms.
Network Inventory
Once you have made your choice for IoT devices, it is important to identify them and to know the properties of these products that you are going to integrate into your computer network. Only if we know, all these devices (inventory) and their characteristics (functionalities) can we dissociate normal activities from any unwanted activity in our network.
Regular monitoring of the local network (Wi-Fi), connected devices and their activity will also detect possible problems and close doors when they are no longer in use.
Network Segmentation
If other vital applications are hosted on the same internal network, it is strongly recommended to separate this network into different segments. One logical segment or network should host and/or interconnect IoT devices, while a second dissociated network would be used exclusively for the hosting of critical information systems.
Network Minimalization
The more IoT devices you put into a network, the more weaknesses and potential security vulnerabilities you introduce. Conversely, this risk can be minimised by making sure to put only the bare minimum of connected devices into one’s network.
Network Filtering
Certain network elements (routers and firewalls for example) allow filtering of information circulating between two networks or network segments. Filtering can, for example, relate to source or destination addresses and ports, communication protocols, content, bandwidth or the volume of information.
In the case of network segmentation, it would be possible to filter information exchanged between two segments and to accept only connections between devices identified beforehand according to a well-defined exchange protocol.
Deactivate/remove non-used devices from your network
Any IoT device integrated into the network has potential vulnerabilities. Also, a device that is not in use may be forgotten in the inventory or security updates. Therefore, do not hesitate to deactivate any device that is not in use.
Dispose of IoT Devices
In case of prolonged non-use or obsolescence, IoT devices must be removed from the network and be discarded. Often IoT devices have a memory that stores information or configurations that reveal aspects related to the security of your network. Do not forget to delete this data from the devices or physically destroy them.
Remove vulnerable interfaces
Several tools make it possible to identify vulnerabilities of certain connected objects, in particular in the context of Bluetooth connectivity.
One such tool is the IoT Inspector developed by the Cybersecurity Competence Center (C3) with the support of private partners. The ever-increasing complexity of connected devices and the demand for security compliance in IoT simply called for a more efficient risk assessment approach. With IoT Inspector, you can automatically discover vulnerabilities and security risks before attackers exploit them.
The threat is very real: read this article 7,339 Vulnerabilities Underneath the Christmas Tree which is about IoT Inspector in action. IoT Inspector’s security experts examined a fictitious Christmas gift basket containing six products from renowned manufacturers and found a total of over 7,000 vulnerabilities…
8. The rise of the machines: are we prepared?
‘Despite continued security problems, the IoT will spread and people will become increasingly dependent on it. The cost of breaches will be viewed like the toll taken by car crashes, which have not persuaded very many people not to drive.’ — Richard Adler
The principle of IoT is a fantastic idea, but whether it becomes a nightmare for us to deal with or not mainly depends on how well we can keep the whole IoT lifecycle under control. The more devices we connect to the Internet, the more we increase the potential for cybercrime.
8.1 Smart Home Solutions
Intelligent devices in our homes (Smart Home) can communicate with each other and at the same time open up new vulnerabilities which can be exploited by cybercriminals. Insufficiently encrypted connectivity may enable attackers to access the entire home network including the smart home applications.
We should admit that it is much easier to buy a new device and then another one than to administer how many devices we have, whether they are working properly, running the latest firmware, none of them have been attacked unauthorized, and so on.
It is easy to confess that instead of handling the devices separately, after a while, we are forced to think in a system and handle them as a unit against cybersecurity threats.
And the reality is not far from the hype: sometimes we can read amazing news e.g. like cybercriminals hacked a refrigerator and had it sent out spam emails while it was making ice cubes. Following this line of thought, we can get to the point where our smart devices take control and when we get home after a tiring day this picture ‘welcomes’ us at home:
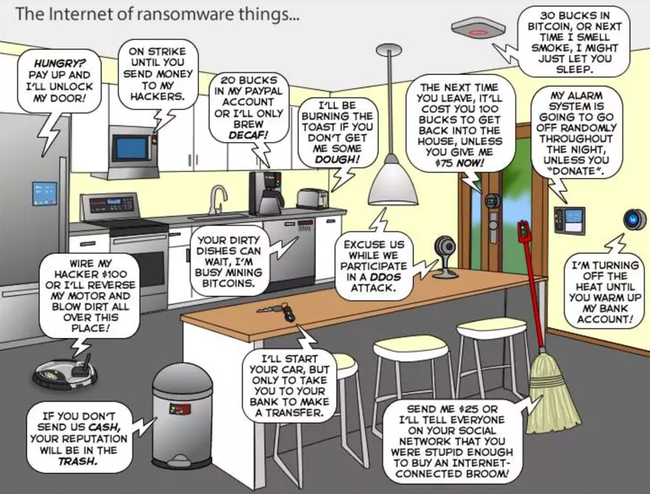
Ransomware – The Dangers of Digital Currency (Joy of Tech)
With the advantages of smart home technologies, the dangers and security risks for their users grow accordingly. Cybercriminals who have gained access to our home network can manipulate intelligent household devices. Moreover, criminals can access sensitive personal information, and by abusing them they can blackmail us.
These attacks are more difficult to track as the world of Internet-connected devices expands far past laptops and tablets.
With PHYSEC Guard (for keyless entry systems), you may control your smart home devices conveniently, securely, and without access to data via your smartphone. PHYSEC Guard can protect you from relay attacks (a passive man-in-the-middle attack designed to bypass authentication without being close). This solution can be used for secure and trustworthy access control in a smart home solution.
8.2 Smart City Solutions
Today, over 55% of the world’s population already live in urban areas. Smart cities can provide an answer to the global challenges posed by rapid urbanisation, population growth and climate change. Luxembourg authorities, academia, and the private sector have cooperated on several Smart City projects in the framework of the Digital Luxembourg initiative in the past few years (Hollerich Village, Smart City Energy platform, GOLIATH project, ICE Gateway, etc.)
In smart cities, anyone can access and use data from public infrastructures. The UBIRCH solution with its cryptography and blockchain technology ensures that data within the IoT system created is authentic and untampered with at its point of origin and maintain this protection over the entire lifetime of the data. Whether it is waste management, traffic management, or securing the critical infrastructure of a city, data integrity is essential to the safe operation of the city’s infrastructure.
The collaboration between POST Luxembourg and Software AG is a real success story: It took POST less than six weeks to build a complex and secure IoT system using Software AG’s Cumulocity IoT to implement and launch a complex smart city project.27
Laurent Rapin, IoT Solution Advisor at POST said: ‘With Cumulocity IoT, our customers will be able to better manage their resources, parking, water, environment, efficiently control energy usage, manage traffic, and take advantage of numerous other applications.’
ENISA Good practices for IoT and Smart Infrastructures Tool
This tool intends to provide a quick guide for operators and industries in the field of IoT to do their own risk assessment. According to ENISA’s recommended security good practices, you can identify threats and prioritise security areas of importance.
The tool lists security good practices for IoT in five areas: Smart Cities, Smart Cars, Smart Airports, Industry 4.0, and Smart Hospitals.
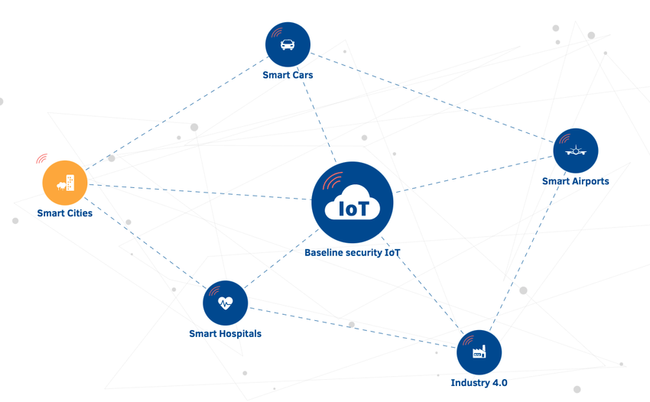
Visit the ENISA Good practices for IoT and Smart Infrastructures Tool website, select one from the five areas that are most relevant for you, and review the updated table with security measures/good practices offered, threat groups displayed and apply the suggestions to your own situation. The biggest benefit of such tools is that they are compiled by specialists who have meticulously considered what security issues might occur in a particular area. By going through the suggestions and criteria, you can test how well our own system meets the security standards and expectations.
9. Detect and React: You are not alone!
‘And just like any company that blissfully ignored the Internet at the turn of the century, the ones that dismiss the Internet of Things risk getting left behind.’ — Jared Newman
This chapter briefly lists and presents the companies that are part of the Luxembourg Ecosystem and provide IoT solutions.
9.1 Atos
‘Atos is positioned to prepare, implement, and manage sustainable long-term security models, crafted to individual industry sector conditions, for bold IoT and IoE adoption.’
Atos is a French multinational IT company. In terms of cybersecurity, Atos focuses on GDPR solutions, governance, risk and compliance, IAM, IoT security, managed security services and protected business-critical applications.
Atos ensures IoT security at every level: data encryption and integrity; device authentication; identity governance; and application and cloud security management. Atos also provides predictive analytics on their IoT solutions, giving an extra layer of security: prevention and effective intervention can be done on IoT solutions by using their advanced analytics solutions.
9.2 Verizon
Verizon is a global leader delivering innovative communications and technology solutions: Verizon is one of the largest communication technology companies in the world.
NV Verizon Belgium Luxembourg SA operates as a subsidiary of Verizon Communications Inc. They identify your company’s vulnerabilities and design a cybersecurity strategy that addresses them.
Verizon provides holistic protection against today’s security issues: cyberattacks on digital networks and corporate assets. Their intelligence-driven security helps you prepare, recognise, and respond to breaches quickly. Verizon IoT Security Credentialing integrates leading-edge security into IoT on three levels: an over-the-top layer of security, authentication, and encryption.
9.3 Conostix S. A.
Conostix provides you with excellent security and system services in Luxembourg. Their engineers provide high-level quality with a security-driven mind. The company’s mission is to leverage your existing infrastructure and assist you with efficient security management.
Conostix has large expertise in complex security-oriented projects. They deliver high-level security management consultancy to improve your enterprise-wide security strategy. The company’s strategy is oriented towards product development in a niche of the security market: centralised security management.
Conostix has designed and developed the IPFC technology to keep control over a wide and disparate IT infrastructure by collecting all events happening in that infrastructure, enabling a correlation of information on which appropriate actions can be taken. The IPFC technology allows a fast deployment in any existing infrastructure and allows to evolve at a reduced cost, independently of any security vendor or manufacturer.
9.4 DXC Technology Luxembourg S.A.
DXC is an end-to-end IT services company. In terms of cybersecurity, DXC offers intelligent security operations, identity and access management, data protection and privacy, security risk management and infrastructure and end-point security.
9.5 Grant Thornton
Grant Thornton Technology Hub provides cybersecurity services, like penetration tests, cybersecurity for IoT, cybersecurity for the satellite industry, IT forensics, etc.
They deliver an entire value chain of consultancy, training, and tools required for innovative & disruptive technology projects. They can do that by having a multi-disciplinary team, with relevant experience in blockchain, cybersecurity, and innovation, to roll out any complex and innovative projects.
9.6 Comarch Luxembourg
Comarch is a provider of software and IT services. Their philosophy is based on excellence in the implementation of cutting-edge IoT solutions for its customers.
Comarch IoT Platform is the company’s IoT solution that allows process definition, device management, remote control, real-time decisions, and data gathering. It stores and analyses a vast amount of data to support strategic decisions regarding IoT in different sectors, like energy, automotive, retail, manufacturing or healthcare.
9.7 Excellium Services SA
Excellium consultants assist enterprises to perform business and risk assessments, define security policies and procedures, respond to security incidents, and deliver computer forensics services.
Excellium also offers a range of services that help to keep an organisation’s security infrastructure in an optimal state. These services include reviewing security architectures or designing a new infrastructure based on specific requirements.
Excellium security professionals also conduct penetration tests and vulnerability assessments and implement best-of-breed security products.
9.8 Digora Luxembourg
Digora administers and optimises databases. Digora’s solutions cover three areas: Consulting & Digital Transformation, Provision, and Hosting of IT Infrastructure & Managed Services. In terms of cybersecurity, Digora offers penetration testing of security systems and vulnerability scans.
9.9 EKXEL, S.à r. l.
EKXEL IT Service is a consulting company specialising in IT Services, Financial Engineering, Project Management, Business Analysis & Organisation.
Its IoT cybersecurity services begin with consultancy to define a cybersecurity plan and then includes surveillance and protection services.
9.10 SONN PSF S.A.
Sonn PSF is an IT security consultancy company. It offers audits of network and application security and support for the design of network infrastructure and security management. Sonn uses Tier IV data centres.
9.11 SEC Consult Luxembourg S. à r. l.
SEC Consult is one of the leading consultancies in the field of cyber and application security. The company specialises in information security management, security audits, penetration testing, ISO 27001 certification support, cyber defence and secure software certification.
SEC Consult offers a full spectrum of security assessments, be it hardware, firmware, apps or IoT cloud platforms. Their experienced experts check all sorts of IoT devices as well as IoT ecosystems and embedded systems for vulnerabilities and security gaps. SEC Consult is part of Atos.
9.12 OQ Technology S. à r. l.
OQ Technology Sarl is building a global satellite constellation dedicated to ‘Internet-of-Things’ communication that can provide connectivity anywhere, especially in remote and rural areas. With their end-to-end solution and connectivity platform, you will be able to manage, track, and command your assets in a secure, reliable, and easy manner.
‘Critical Assets require secure and extensive monitoring and control. Such a monitoring system should be fault-proof with a backup telecommunication alternative. Our secure and reliable solution fits exactly into this category and can be installed as a prime or a backup solution to government and enterprise-critical assets.’
9.13 Econocom Digital Security S.A.
Econocom assists companies with digital transformation. The company offers digital transformation products and solutions, technology management and cybersecurity-related services such as EMM (Enterprise Mobility Management) and MTD (Mobile Threat Defense). The managed security services include proactive monitoring, incident management and corrective measures, log archiving, analysis and maintenance.
Digital Security was founded in 2015 by a group of experts in computer security and with the support of the Econocom Group. As the name suggests, the corporation aims to help companies permanently improve the way they protect their information and support them in securing their digital transformation and the opportunities offered by the IoT.
9.14 Expeto Wireless
Expeto removes the barriers to digital transformation, by providing enterprises with their own private, agile, and scalable cellular (4G/LTE) networks – but deploy it like Wi-Fi – globally.
Expeto is a venture-based start-up that enables enterprises to interconnect both public and private IoT deployments through a single pane of glass that is easy to configure and cost-effective to deploy. Private networking over LTE translates into LTE connected devices which comply with enterprise security policies and can be delivered at the speed at which the business needs to move.
10. Test and Improve: How can SECURITYMADEIN.LU help? - Updated
‘By letting the IoT devices into our everyday life, it is not like we entered the zoo, but we released the animals into our world.’ — Csaba Gabor
While ANSSI and GOVCERT serve the public sector, SECURITYMADEIN.LU considers the support and service of the private sector to be its most important task.
It also organises the collection, information gathering and information management of crucial services provided by the Luxembourg Ecosystem, maps their availability within the ecosystem and enhances potential collaboration among them. It also promotes, in collaboration with Luxinnovation, the ecosystem within the Greater Region and in Europe.
10.1 SECURITYMADEIN.LU
SECURITYMADEIN.LU is the cybersecurity agency for the Luxembourg economy and municipalities: its three departments (C3, CASES, and CIRCL) help achieve its goals.
10.2 CASES
The CASES (Cyberworld Awareness and Security Enhancement Services) department’s main focus is to offer prevention guidelines and support for companies that are just starting out in the deployment of cybersecurity. To this end, its core mission is to provide awareness-raising, training, and tools like Fit4Contract, Fit4Cybersecurity for the private sector actors.
CASES has developed MONARC (Optimised Risk Analysis Method), allowing precise and repeatable risk management. The way how MONARC handles IoT-related risk management is the ‘IoT Model,’ or more precisely, an asset, which has been developed in cooperation with ANSSI.LU to be included directly in a risk analysis. This asset is dedicated to people using IoT devices, not to people creating such kinds of devices. It is a modular asset with seven components as follows:
- Actuator: avoid a wrong action of your device by handling actuator dysfunction
- Communication interface: prevent the risk of a weak interface, like eavesdropping or DDoS
- Device: manages the physical security of your IoT device
- Local storage: ensures that no data is lost if an asset is destroyed and no information is disclosed in the event of recycling
- Operating system: manages the risks about the OS (e.g. malware, updates, etc.)
- Software: manages the risks in case your device has a user interface
- Sensor: manages the risks of receiving information from an untrustworthy source in case your device has a sensor
With those components, you can create your own IoT object. For example, if you have an IP camera without local storage, you will compose your asset with all the components, except the local storage.
10.3 CIRCL - updated
The CIRCL (Computer Incident Response Center Luxembourg) team gathers, reviews, reports, and responds to computer security threats and incidents. Its team members fight in the front line of cyberattacks and provide first aid following a cyberattack: CIRCL is the CERT (Computer Emergency Response Team/Computer Security Incident Response Team) for the private sector, communes, and non-governmental entities in Luxembourg.
CIRCL has developed a platform (MISP – Open Source Threat Intelligence Platform) for sharing information on the cyberthreats and – attacks in Luxembourg to disseminate the knowledge accumulated in this field and help companies to protect themselves from them.
The D4 Project is a large-scale distributed sensor network project to monitor DDoS and other malicious activities by CIRCL and co-funded by the Innovation and Networks Executive Agency (INEA). This open-source, distributed and collaborative security monitoring platform collects and analyses DDoS information from multiple types of Internet-based networks, then disseminate it real-time to CSIRTs platforms by using MISP (Open Source Threat Intelligence Platform). The aim of the D4 Project is to make the creation and maintenance of such a network simple and efficient.
VARIoT (Vulnerability and Attack Repository for IoT) is an EU project co-financed by CEF (Connecting Europe Facility) to provide actionable information regarding the Internet of Things. The scope of the project is to create vulnerabilities and exploits database dedicated to IoT, provide a large-scale systematic mapping of IoT devices on the Internet, and create mechanisms of active monitoring and harvesting of information of IoT devices.
One of the aims of the VARIoT project is to improve this situation by disseminating open data related to cybersecurity metrics in the field of IoT. To help achieve this goal, as a member of the VARIoT consortium, CIRCL redistributes some of the data generated by partners such as Shadowserver. The VARIoT vulnerabilities and exploits databases have also been published recently.
The data set, which contains data about infected IoT devices detected primarily by exposed IoT devices, is generated daily by Shadowserver. The Shadowserver is a nonprofit foundation that conducts day-to-day network discovery to identify potentially vulnerable devices available through the Internet. Besides that, it notifies the owners of the affected networks and the national CSIRTs responsible by country code.
CIRCL keeps the data (generated by the source) as raw as possible to avoid information loss and maximise data utilisation. The data set is constantly evolving due to emerging new, evaluable vulnerabilities.
The so-called ‘open-data-security description format’ is used to ensure an interoperable description of the dataset collected in security monitoring and analysis. This format (a JSON standard) describes who validated the data, the frequency of the update, and the data sources. Besides the above, this standard also details how the data was gathered and evaluated.
VARIoT also creates an interface to share data, including real-time publication on the EU Open Data Portal and integration with the MISP platform. Therefore, information on IoT, such as data on infected and exposed devices, can be downloaded from the European Open Data Portal and available on the Opendata portal of CIRCL.
In the D4 Project and VarIOT, CIRCL is monitoring activities of networked devices (network equipment, smart TV, etc.) which are in the set of IoT devices. There are many incidents
related to such equipment, and the D4 Attack Map is a visual representation of real-time SSH brute force attacks against such equipment.
10.4 C3 - updated
The C3 (Cybersecurity Competence Center) is a skills center that supports organisations both in their digital transformation and also in improving the skills of their employees. C3 has three competence areas as follows:
- Threats and vulnerabilities observatory (become aware of the latest threats and vulnerabilities)
- Testing facility (test your cyber resilience)
- Training and simulation platform (attend training or simulations (like Room #42) to better prevent and react to incidents)
Room#42 is the flagship solution of C3, an innovative and unique concept: it is a cyberattack simulation game, where participants can fully immerse in a cyberattack simulation.
Some specific categories of IT devices are more and more widespread. But being heavily automated by design and having an intended usage that requires minimal interaction with their users, if any, they tend to be overlooked when systems are being secured and certainly not managed as information systems.
IoT devices (temperature sensors, webcams, smart locks, printers, fridges, etc.) are most of the time embedding some aspect of Internet technology, often for maintenance and configuration purposes.
As part of the development of its Testing Platform, aimed at making some of the most critical tests affordable for a larger share of the ecosystem, C3 initiated a partnership with two European security companies, Sec Consult and IoT Inspector. They are the creators and maintainers of “IoT Inspector”, a comprehensive set of tools and services that allows performing in-depth technical assessments of the firmware.
In order to enable organisations to be aware of what type of vulnerability or exposure they are adding to their systems when deploying such devices, it is possible through the Testing Platform to test the firmware of the most common IoT’s. A first partnership was established with one of the leading European companies for IoT assessments: IoT Inspector.
Organisations from Luxembourg can register for a test of a given IoT firmware through the Testing Platform and get a comprehensive report from our partner. One of the critical use cases of such testing is to strengthen the procurement process of IT devices and systems by independently assessing a so-called “smart device” before its acquisition and deployment.
Weaknesses such as the use of hardcoded credentials, outdated libraries, hidden connections to the maker’s systems can be uncovered and reported. This will definitely help to strengthen the procurement process by allowing an informed conversation with the provider. Once the IoT is deployed, IoT Inspector will also allow to monitor the occurrence of possible mishaps, vulnerabilities or needs for updates. IoT Inspector does not only examine the IoT device’s firmware for vulnerabilities but also ensures compliance with international security standards – without requiring access to source code or network or physical access to the IoT device. You need to upload the firmware, start the analysis, and a few minutes later the results will be available for you.
In order to benefit from such a service, companies based in Luxembourg can register on the C3 Testing Platform at testing.c3.lu and require a test. They will be guided in the process to provide the firmware to the testing platform and get a comprehensive report once the assessments will have been run.
- IoT Inspector does not only examine the IoT device’s firmware for vulnerabilities but also ensures compliance with international security standards – without requiring access to source code or network or physical access to the IoT device.
- The VARIoT (Vulnerability and Attack Repository for IoT) project is an EU project to provide actionable information regarding the Internet of Things. The scope of the project is to create vulnerabilities and exploits database dedicated to IoT, provide a large-scale systematic mapping of IoT devices on the Internet, and create mechanisms of active monitoring and harvesting of information of IoT devices.
- In the D4 Project and VarIOT, CIRCL is monitoring activities of networked devices (network equipment, smart TV, etc.) which are in the set of IoT devices.
- There are many incidents related to such equipment, and the D4 Attack Map is a visual representation of real-time SSH brute force attacks against such equipment.
11. Conclusion
‘I don’t care how secure you think your organisation is, I’ll social engineer my way inside in less than 24 hours regardless of the sophistication of your IoT microcosm security. Whatever obstacles I run into exploiting your technical vulnerabilities will be made up for by exploiting the vulnerabilities in the cyber hygiene of your staff.’ — James Scott
The Internet of Things offers countless new opportunities and undoubtedly has many benefits, but it is not harmless. Connecting the devices to the Internet allows us to communicate with each other, which is not only convenient for us but also an environmentally friendly and time-saving solution. However, the security of the devices is in doubt, and the potential for virus infections and hacker attacks is high.
Recognising the significance of the threats, SECURITYMADEIN.LU launched a large national awareness campaign in collaboration with ANSSI and SIGI. A dedicated website, videos, posters, and a flyer have been produced to bring the message to the general public.
Probably the first and most important step is to raise awareness of the dangers of IoT among people, and this awareness raising has to take place at two levels: manufacturers must make connected objects more secure, and users must select their IoT devices with much more care and use them more thoughtfully.
The best approach in fighting against IoT-related risks would be to define acceptance standards for these products in our markets according to criteria related to cybersecurity.
Legal regulation cannot keep up with the pace of technological development and so we cannot wait for the emergence of such regulations to adapt our behaviour. It is in our interest to recognise and face the dangers of IoT and we must master best practices such as
- verify that the object that you want to buy allows the modification of your password
- after installation change passwords
- ensure the physical protection of the object
- update regularly and as soon as a new update is available
The use of IoT products are going to continue to grow and businesses will have to prioritise security over innovation and promote the implementation of security by design in 2022.
Emerging IoT technologies have already changed our lives; yet, more challenges need to be faced and handled: the future of IoT is virtually unlimited due to advances in technology and consumers’ desire to integrate devices.
To quote Ben Parker:
‘With great power comes great responsibility.’
This is even more true in the technological field where it is important to consider and find the right balance between privacy, risks, and benefits of these new technologies.
Revisions
- Original document: 03/01/2021
- First revision: 10/02/2022, Chapters 10.3 and 10.4 were updated